The New Phishing Attack Not
Blocked by Your Current Cyber
Defense
Roger A. Grimes
Data-Driven Security Evangelist
Malicious Browser Notifications

Roger A. Grimes
Data-Driven Defense Evangelist
KnowBe4, Inc.
Twitter: @RogerAGrimes
LinkedIn: https://www.linkedin.com/in/rogeragrimes/
• 30 years plus in computer security
• Expertise in host and network security, IdM, crypto,
PKI, APT, honeypot, cloud security
• Consultant to world’s largest companies and militaries
for decades
• Previous worked for Foundstone, McAfee, Microsoft
• Written 12 books and over 1,000 magazine articles
• InfoWorld and CSO weekly security columnist 2005 -
2019
• Frequently interviewed by magazines (e.g. Newsweek)
and radio shows (e.g. NPR’s All Things Considered)
About Roger
Certification exams passed include:
• CPA
• CISSP
• CISM, CISA
• MCSE: Security, MCP, MVP
• CEH, TISCA, Security+, CHFI
• yada, yada

3
Roger’s Books

2
• The world’s largest integrated Security Awareness Training
and Simulated Phishing platform
• Based in Tampa Bay, Florida, founded in 2010
• CEO & employees are ex-antivirus, IT Security pros
• We help tens of thousands of organizations manage the
ongoing problem of social engineering
• Winner of numerous industry awards
About Us

5
Learn
• Notification basics
• How legitimate websites are targeted to deliver
these stealthy phishing attacks
• Why browser notification phishing attacks bypass
your cyber defenses
• Other sneaky browser attacks the bad guys use to
infiltrate your network
• How to shore up your defenses and to protect
against them all

6
For decades, malware writers and phishers have exploited “transitive” trust:
• Banner ads
Typical scenario#1:
1. Legitimate vendor asks trusted marketer for help with web campaign
2. Marketer reaches out to trusted web campaign firm for help
3. Web campaign firm promises a certain number of views
4. Web campaign firm subcontracts with another sometimes dodgy vendor who is really
adware group
Typical scenario#2:
1. Malware/phisher group poses as legitimate company and buys ads
2. They create online content for display in ad
3. Legitimate content is switched out for malicious content when wanted
Before Notification Maliciousness

7
For decades, malware writers and phishers have exploited “transitive” trust:
• Malicious banner ad campaigns
• Very sophisticated
• One innocent-looking element replaced
• Ex: https://www.domain.com/counter.html
• Original URL points to a normal “counter” applet
• Then counter.html is switched out on the fly with malicious JavaScript
• Not shown to anyone legitimate involved with ad buy/sell
• People checking reports of maliciousness don’t find anything wrong
• Fact: Most major websites have no clue about what is executing on their web sites
• 50% to 90% of all client-side executing code is from third parties
• Much of it is not good
• Many companies hiring companies, like The Media Trust, dedicated to quickly detecting
maliciousness on legitimate web pages
Before Notification Maliciousness
8
For decades, malware writers and phishers have exploited “transitive” trust:
• Banner ads
• Rogue applets
• Code snippets
• “Must retain counter to reuse” or “Must retain source URL to reuse”
• Web site “well poisoning”
• And now hackers/phishers are starting to abuse browser/desktop notifications
• Google says
Before Notification Maliciousness

9
Learn
Notification
Basics

10
• Known as browser/desktop notifications or push notifications
• Allows display messages to be sent to user outside of their browser/tab or app
after the notification permission was given by the user
Notification Basics

11
• Each app/website must first ask user permission to send future notifications
• Default
• User can be asked to approve; else deny by default
• Granted
• User approved, future notifications can be sent
• Denied
• User denied, notifications cannot be sent for that app or website
Notification Basics

12
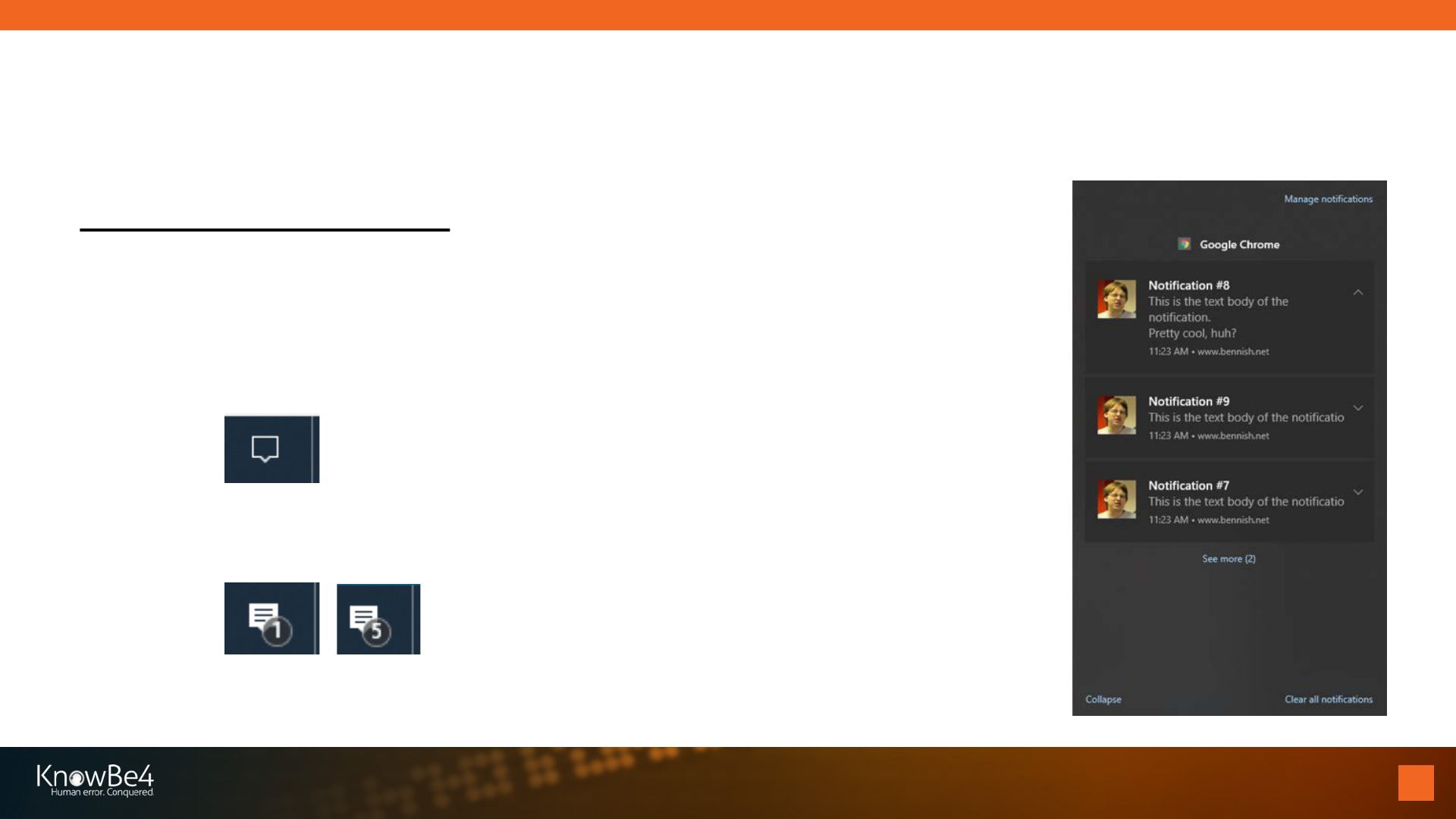
Desktop notifications
• May be shown on desktop over other apps or a gentle reminder shown
• Windows 10 shows an empty message dialog box in lower right taskbar when there are no
notifications waiting
• Shows a message dialog box along with notification message count when notifications are
waiting
Notification Basics
13
Desktop notifications
• May be shown on desktop over other apps or a gentle
reminder shown
• Windows 10 shows an empty message dialog box in lower
right taskbar when there are no notifications waiting
• Shows a message dialog box along with notification message
count when notifications are waiting
Notification Basics

14
• Based on a standard to allow developers to send messages to end-user's
cross-platform using a single programming method
• Early versions introduced around 2009 (known as JavaScript Desktop
Notification API then)
• W3C introduced an updated HTML5 version called the Notification API in
2014 (may be treated/merged with Push Notification API)
• Started to be more abused in 2019
• Browsers and operating systems must support the Notification API
• Supported on Microsoft Edge, Google Chrome, Apple Safari (desktop only),
Opera, Mozilla Firefox, but not Internet Explorer
• Desktop and mobile versions may support different feature sets
Notification Basics

15
It’s Even an RFC (Request for
Comments)
• RFC 1030 - Generic Event Delivery
Using HTTP Push
• Created Dec. 2016
• RFCs are essential Internet standards
and rules
• https://tools.ietf.org/html/rfc8030
• Originally used registered port TCP
1001, but now uses 443 to get past
firewall issues
Notification Basics

16
Browser Version First Supported
• Chrome version 22
• Edge version 14
• Firefox version 22
• Opera version 25
• Safari version 7
*Not all features supported by all browsers (for example, Safari does not support
opening new browser windows)
Notification Basics

17
Notifications Service Workers
• Each allowed notification process is called a “service worker” in developer-
speak
• Service workers can update themselves, changing what they display and do
• Service workers can install other service workers
• Service workers can modify network content from their own pages
• So what you see may not be what you get
• They don’t need your permission after the first allow
• Be careful of giving that initial trust
Notification Basics

18
Service Workers in General
• “A service worker is a JavaScript file that runs separately from the main browser
thread, intercepting network requests, caching or retrieving resources from the
cache, and delivering push messages”
• From https://developers.google.com/web/ilt/pwa/introduction-to-service-worker
Service workers must be:
• Registered
• They are registered before you get the (first) Allow prompt
• Installed
• Activated
Notification Basics

19
Notifications are Multimedia
• Can display more than just text
• Icons/Emoticons, badges, etc.
• Pictures, content, URL links
URLs significantly increase potential maliciousness
Notification Basics

20
Notifications have Actions
• Can create any button label(s) and link it to allowed actions
• Often limited to two actions at a time
Actions may not always be good
Notification Basics
buttons and labels

21
Notifications Actions
• Code example
self.registration.showNotification(‘New
message from Vendor', {
actions: [
{action: ‘like', title: ‘Like'},
{action: ‘reply', title: ‘Reply'}]
});
Notification Basics
self.addEventListener('notificationclick', function(event) {
var messageId = event.notification.data;
event.notification.close();
if (event.action === 'like') {
silentlyLikeItem();
}
else if (event.action === 'reply') {
clients.openWindow("/messages?reply=" + messageId);
}
else {
clients.openWindow("/messages?reply=" + messageId);
}
}, false);

22
Notifications Actions
• Code example
self.registration.showNotification(‘Import
ant alert from Microsoft
Corporation!!!', {
actions: [
{action: ‘open', title: ‘Open'},
{action: ‘open', title: ‘Ignore'}]
});
Notification Basics
self.addEventListener('notificationclick', function(event) {
var messageId = event.notification.data;
event.notification.close();
else if (event.action === ‘open') {
clients.openWindow((“https://microsoft.com.badurl.com”);
}
else {
clients.openWindow(“https://microsoft.com.badurl.com”);
}
}, false);

23
Some Possible Notifications Actions
• Vibrate mobile devices
• Send sounds
• Display alerts
• Use Unicode characters
• Can open/delete/archive email
• Can initiate dialing telephone numbers
• Can require interaction (user can only click “OK”)
• Have OnClick, OnClose, OnError events
• Can open new browser windows at predetermined URLs
Notification Basics
Growing risk

24
Comments on Notifications Actions
• From https://developers.google.com/web/updates/2016/01/notification-actions
“The interesting thing is that the actions don't have to open up a new window,
they can perform general application interactions without creating a user
interface. For example, a user could "Like" or "Delete" a social media post that
would perform the action on the user's local data and then synchronize it with the
cloud without opening a UI…”
Notification Basics

26
Web Sites/Apps/Organizations Use Notifications
• Many legitimate web sites use
• Many legitimate apps use
• Many legitimate organizations buy and sell access to other site’s and app’s
notifications and the customers who allow them
Notification Basics

27
Push Notification Networks
• Many organizations exist to sell access to other
subscribed notifications forming “push networks”
• Sometimes not so legitimate organizations are
involved
• Table source:
https://trends.builtwith.com/widgets/push-
notifications
Notification Basics
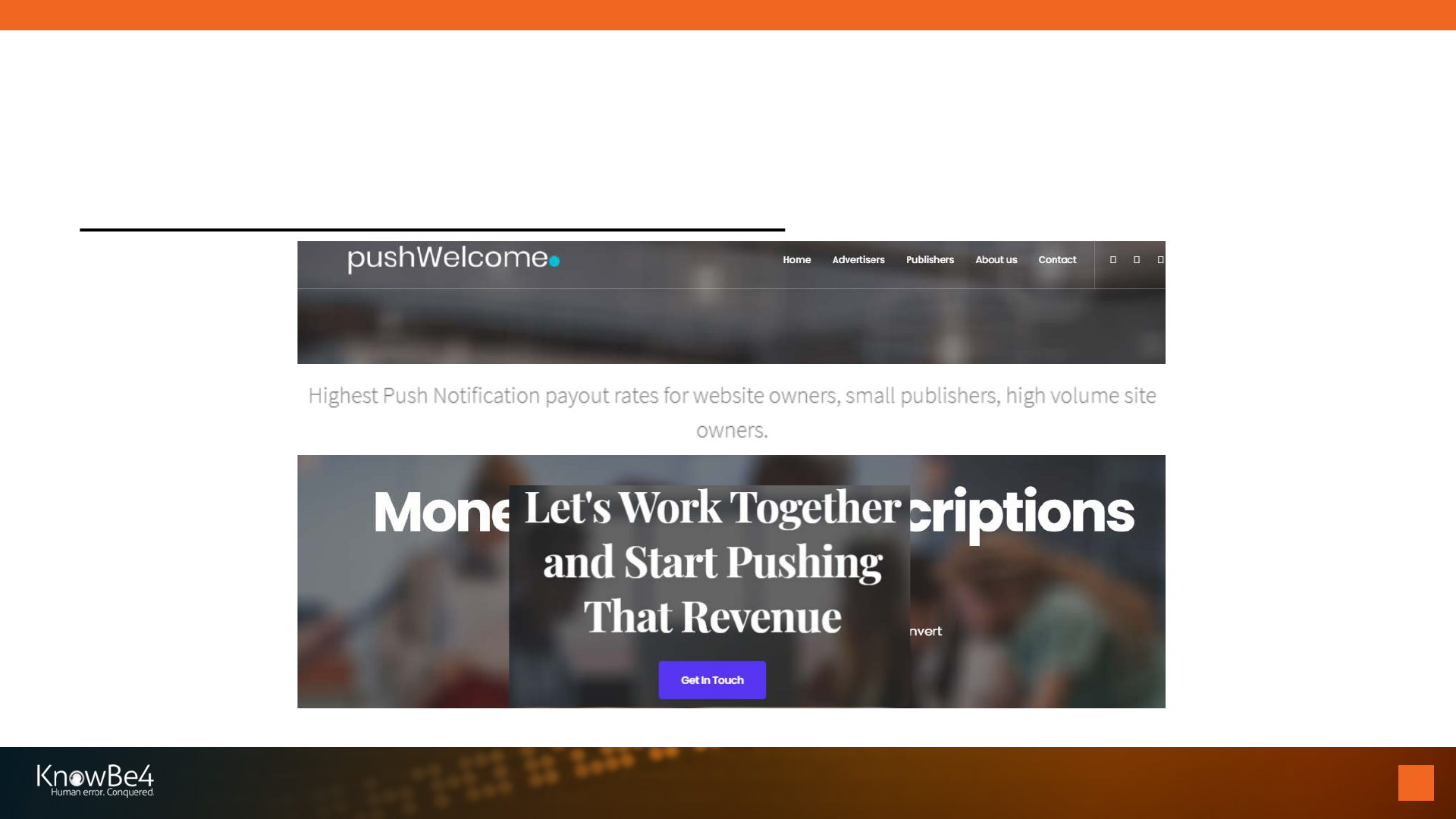
28
Push Notification Monetization Networks
Notification Basics

29
Learn
Malicious
Notifications

30
Example
1. Malware group or push network will pose as 100% legitimate vendor asking
web site to allow their “affiliate” code to be executed when a user allows
notifications
2. At first, all seems legit
3. Later, network switches out harmless code for malicious code
a) When vendor/victim complains, usually malicious network doesn’t respond, is slow to
respond, or denies it’s happening
b) When proven that it is happening, then they say something bad accidentally slipped
through and/or blame it on some other “rogue” person or company who will be “punished”
c) It always seems to take a long time for bad code to be removed
d) Rinse and repeat
Malicious Notifications

31
Headlines
Malicious Notifications

32
Example Maliciousness/Objectives
• Phishing
• Install malware
• Track user’s activities
• Advertisements
• Redirectors
• Maliciousness can be replaced on the fly as wanted
• Often do multiple bad things at once
Malicious Notifications

33
Example Maliciousness/Objectives
Why Notification Phishing Is Especially Dangerous
• Notifications happen outside the app or browser where it was approved
• Can even be displayed on “lock screen”
• Can be used to do credential phishing
• Once initial approval is allowed, the sky is the limit
Malicious Notifications

34
Fake AV Message Example
Malicious Notifications
Example from: https://www.indelible.global/post/pushbug-uncovering-widespread-push-notification-rfc-8030-abuse-in-the-wild

35
Fake AV Message
Malicious Notifications
Example from: https://krebsonsecurity.com/2020/11/be-very-sparing-in-allowing-site-notifications/

36
Fake AV Message
Malicious Notifications
Example from: https://blog.malwarebytes.com/threat-analysis/2018/10/scammers-use-old-browser-trick-to-create-fake-virus-
download//
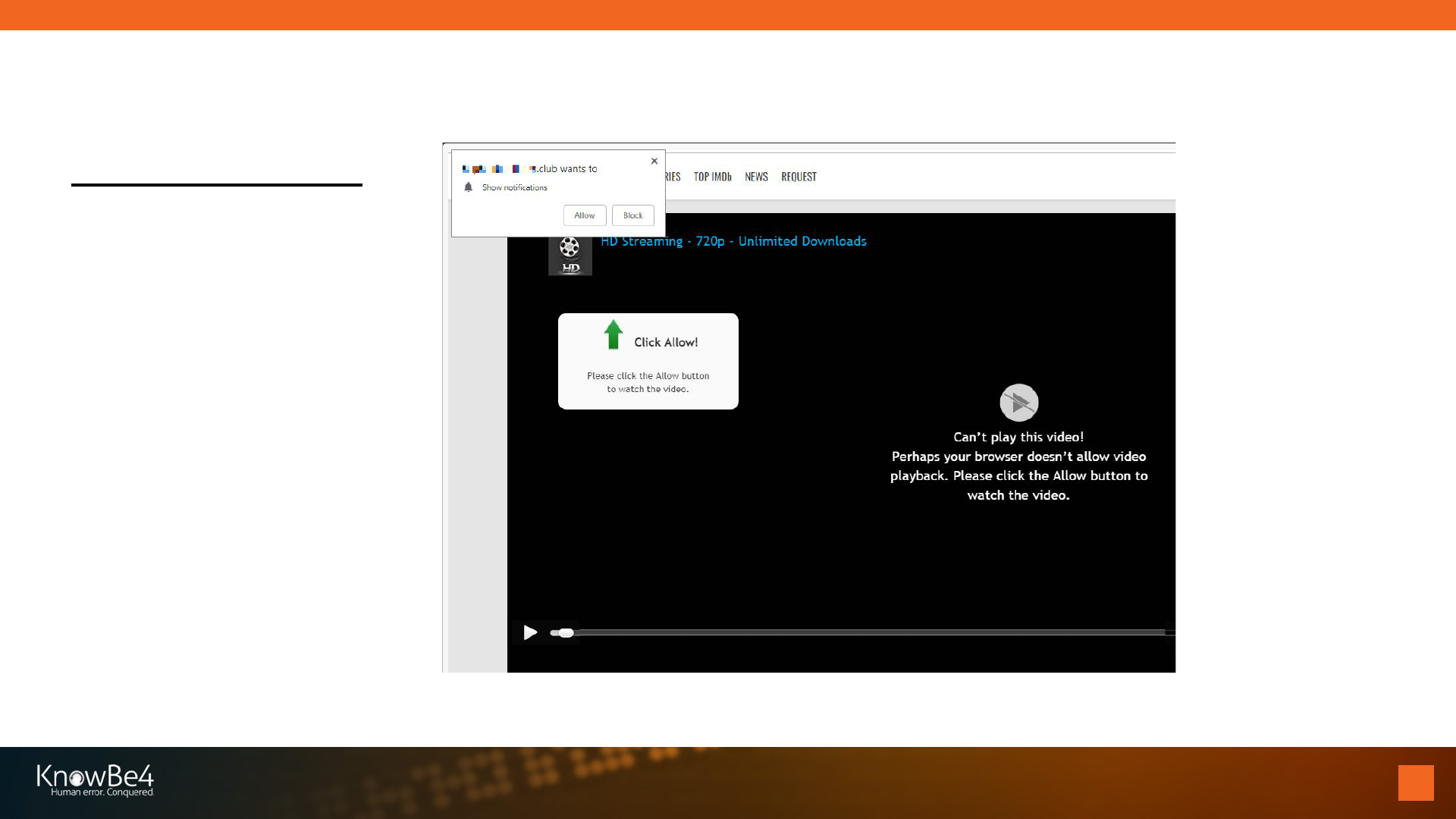
37
Fake Video Error
Malicious Notifications
Example from: https://blog.malwarebytes.com/security-world/technology/2019/01/browser-push-notifications-feature-asking-
abused/
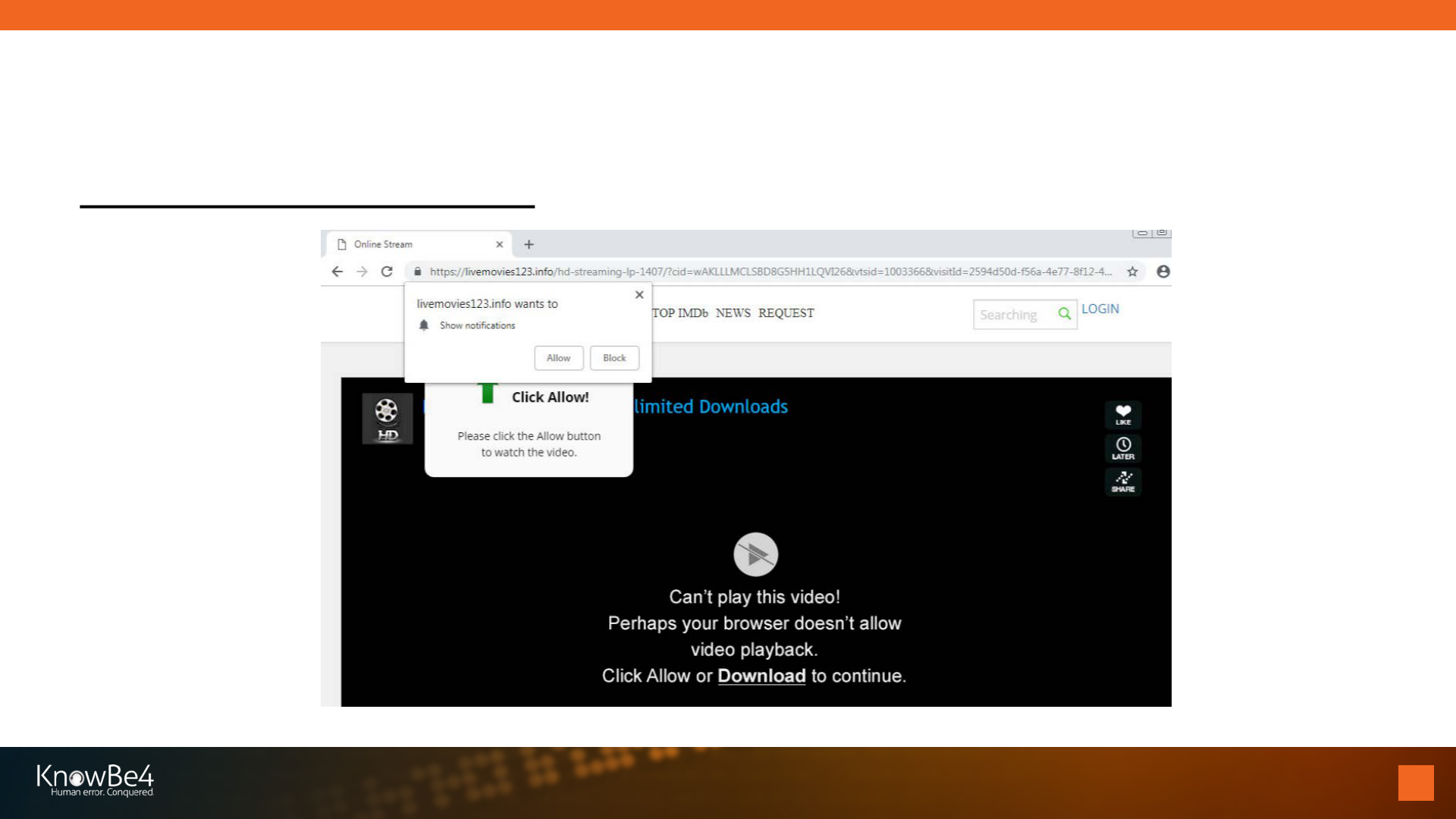
38
Fake Video Error Message
Malicious Notifications
Example from: https://statics.esputnik.com/photos/shares/Blog/images/abusive/image5.png/

39
Verify You’re Not a Robot Scam
Malicious Notifications
Example from: https://www.bleepingcomputer.com/news/security/scam-browser-notification-prompts-increased-by-
69-percent-in-2019/

40
Learn
Defending Against
Malicious
Notifications

41
General
• Relatively new abuse method
• Often coming from legitimately, trusted sites and apps
• Dynamic domain use
• No easy way to review/fix configuration issues
• Victims intentionally “allowed it”!
Note: Some AV vendors are becoming better at recognizing it.
Why Malicious Notifications Evade AV

42
• Anyone can fall victim to social engineering
• “Smart people” are just as likely to fall victim to phishing as anyone else
• Scammers use “stressors” to make people bypass their normal skepticism
survival skills
• Whether or not someone clicks on a “phish” or falls victim to a fake
notification, has more to due with awareness of digital crime than anything
else
• Once people are aware of social engineering, phishing, and all it’s forms,
the less likely they are to fall victim to it
Phishing Cannot Be Beat by Intelligence

43
Defending Against Phishing
General Defense Methods
• Policies
• Technical Controls
• Anti-Malware Software
• Anti-Spam/Phishing
• Content Filtering
• Security Awareness Training
https://blog.knowbe4.com/the-three-pillars-of-the-three-computer-security-pillars

44
Overview
• Education
• Review and remove unneeded existing notifications on desktop and browser(s)
• Configure desktop and browsers to reject notifications by default
• Find out if your AV/EDR solution is aware of malicious notification scams
• Run latest browser versions
• Report notification scam domains to Google and Microsoft
Defending Against Notifications

45
You Can Disable Them In the Browser
• You can enable or disable them globally in the browser or OS
• How you do that varies per browser and OS
Example: Microsoft Edge
Defending Against Notifications

46
You Can Disable Them In the Browser
• You can enable or disable them globally
in the browser or OS
• How you do that varies per browser and
OS
Example: Microsoft Edge
Defending Against Notifications

47
You Can Disable Them In the Browser
Example: Microsoft Edge
Defending Against Notifications
Will globally block if disabled
48
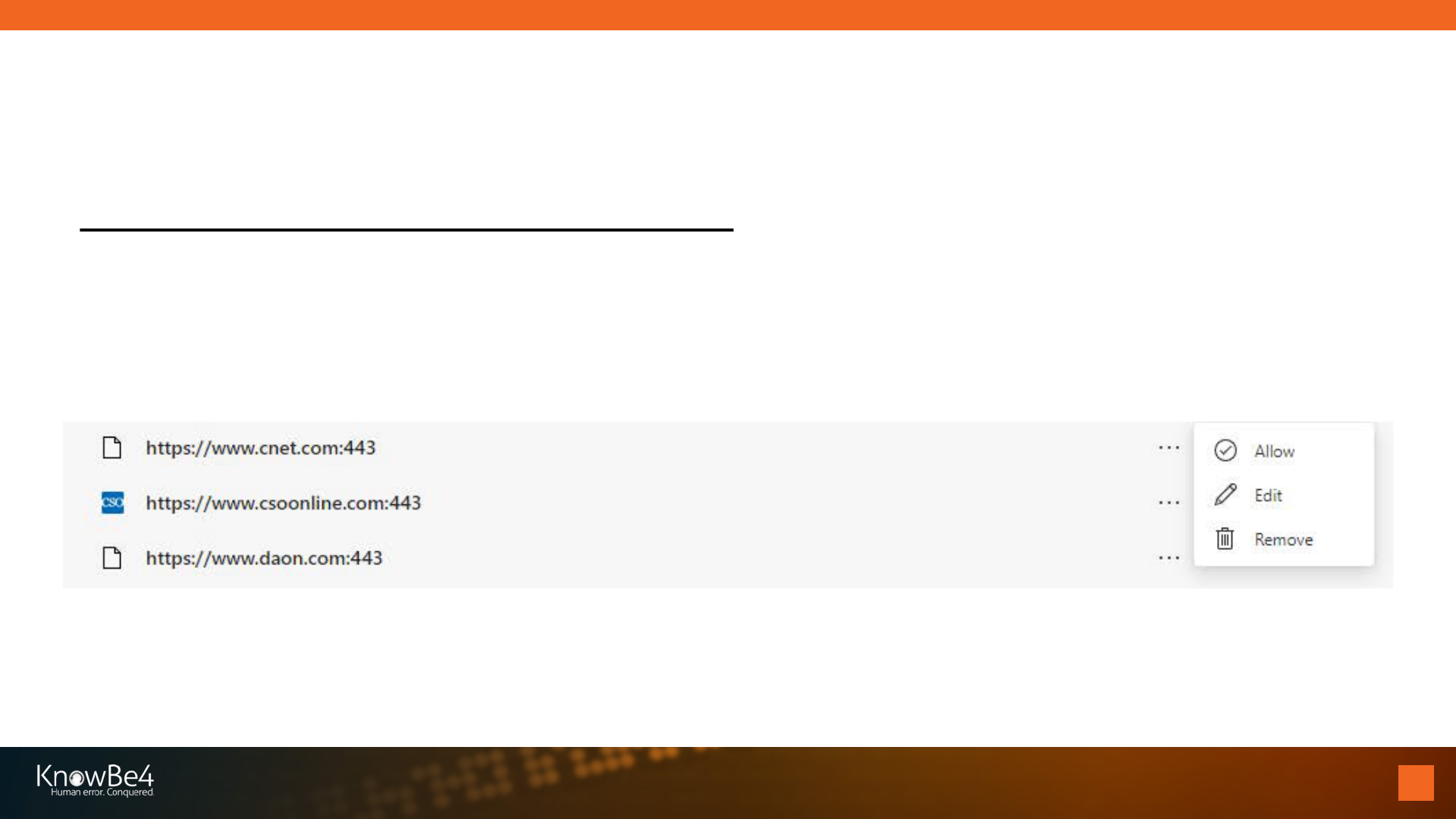
You Can Disable Them In the Browser
Example: Microsoft Edge
Can individually block or allow per site, or if you remove it will allow the site to
ask permission again
Defending Against Notifications
49
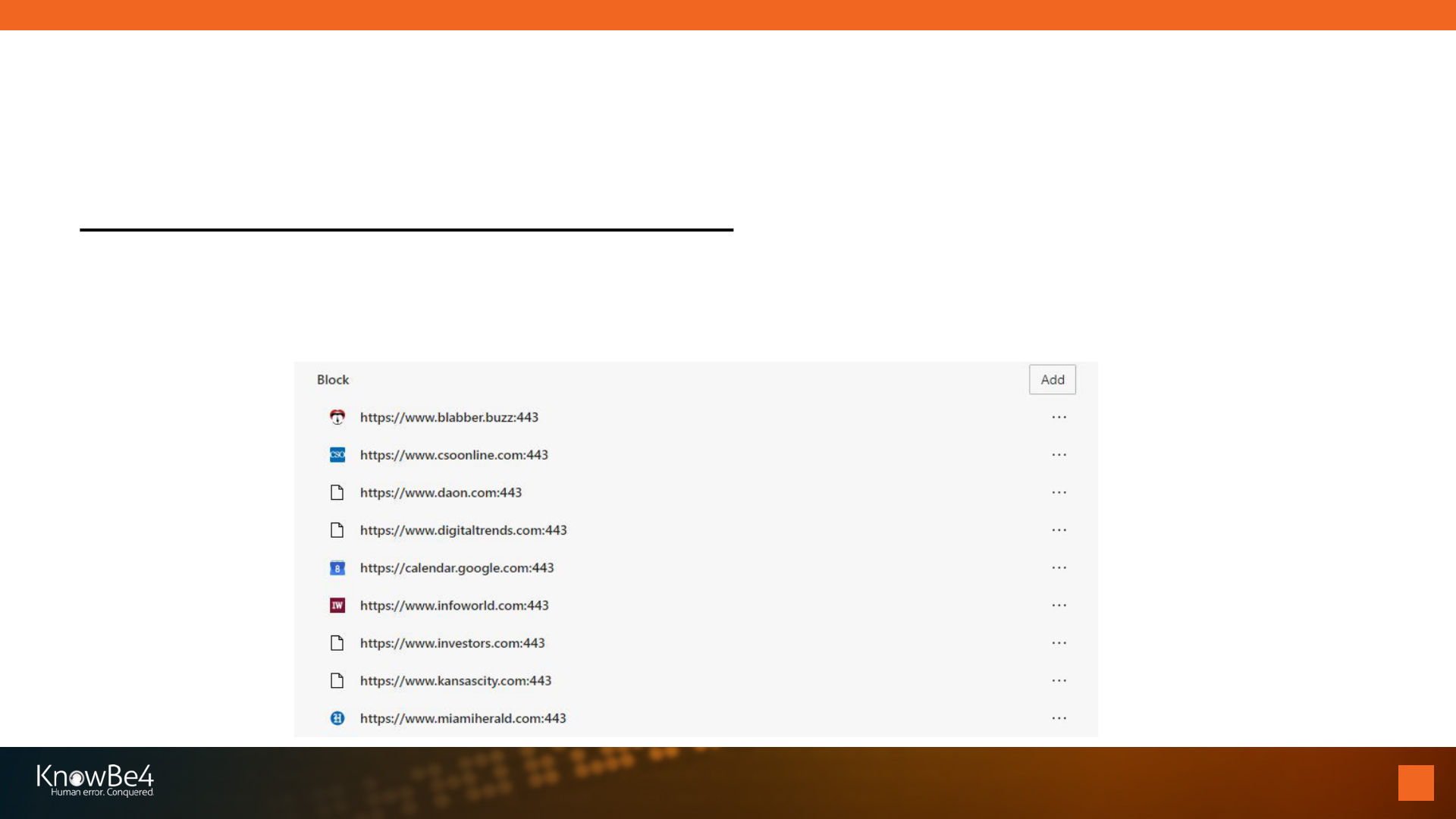
You Can Disable Them In the Browser
Example: Microsoft Edge
These sites have already been denied permission (blocked) and can’t ask again
Defending Against Notifications

50
You Can Disable Them In the Browser
Example: Microsoft Edge
These sites have already been allowed permission (allow)
Defending Against Notifications
Changes often require a tab or browser restart

51
You Can Disable Them In the Browser
Example: Google Chrome
You can configure per site
Defending Against Notifications
chrome://settings/content/

52
You Can Disable Them In the Browser
Example: Apple Safari
• You can configure per site
• Safari > Preferences > Websites >
Notifications
Defending Against Notifications

53
You Can Configure Them In OS
Example: Microsoft Windows
Defending Against Notifications
Settings/Notification & actions

54
You Can Configure Them In OS
Example: Microsoft Windows
Defending Against Notifications
Settings/Notification & actions

55
You Can Configure Them In OS
Example: Microsoft Windows
Defending Against Notifications
Settings/Notification & actions

56
You Can Configure Them In OS
• Example: Apple MacOS
• Apple > System Preferences >
Notifications
Defending Against Notifications
Source: https://support.apple.com/guide/safari/customize-website-notifications-sfri40734/mac

57
Example Step by Step Browser Instructions
• https://blog.malwarebytes.com/security-world/technology/2019/01/browser-
push-notifications-feature-asking-abused/
• https://www.theverge.com/2019/7/18/18716041/website-notification-prompts-
pop-ups-how-to-stop
• https://hackingvision.com/2019/09/25/malicious-browser-push-notifications/
• https://www.androidpolice.com/2020/06/18/track-block-rogue-ads-android/
Remember to disable in OS and browsers
Defending Against Notifications

58
Some Browsers Will Warn You If They Recognize Potentially Malicious
Notifications
• https://blog.chromium.org/2020/10/reducing-abusive-notification-content.html
• Google proactively subscribes to notification pushes and monitors behavior
• They will warn users if notification request comes from a known rogue domain
• Chrome browser v. 80 (released Feb. 4, 2020) and above have this feature
Defending Against Notifications

59
Some Browsers Will Warn You If They
Recognize It
• https://blog.chromium.org/2020/10/reduci
ng-abusive-notification-content.html
• Google proactively subscribes to
notification pushes and monitors behavior
• They will warn users if notification request
comes from a known rogue domain
• Chrome browser v. 80 (released Feb. 4,
2020) and above have this feature
Defending Against Notifications

60
Report Sites With Malicious Notifications
• https://safebrowsing.google.com/safebrowsing/report_phish/
• https://www.microsoft.com/en-us/wdsi/support/report-unsafe-site-guest
Defending Against Notifications

61
Resetting Browser Settings Automation
• 3
rd
party device management programs which allow application/registry setting
editing
• Microsoft Edge
• Requires custom Administrative Template and Group Policy or Microsoft Intunes
• https://www.techrepublic.com/article/how-to-manage-the-new-microsoft-edge-through-
group-policy/
• Google Chrome
• https://support.google.com/chrome/a/answer/188446?hl=en
Defending Against Notifications

62
Education
• Share this presentation
• General security awareness training, including specific training on notification
phishing
Good links to review and share:
• https://www.indelible.global/post/pushbug-uncovering-widespread-push-
notification-rfc-8030-abuse-in-the-wild
• https://krebsonsecurity.com/2020/11/be-very-sparing-in-allowing-site-
notifications/
Defending Against Notifications

63
KnowBe4 Security Awareness Training
Baseline Testing
We provide baseline testing to assess the Phish-Prone™
percentage of your users through a free simulated phishing attack.
Train Your Users
The world's largest library of security awareness training content;
including interactive modules, videos, games, posters and
newsletters. Automated training campaigns with scheduled
reminder emails.
Phish Your Users
Best-in-class, fully automated simulated phishing attacks,
thousands of templates with unlimited usage, and community
phishing templates.
See the Results
Enterprise-strength reporting, showing stats and graphs for both
training and phishing, ready for management. Show the great ROI!
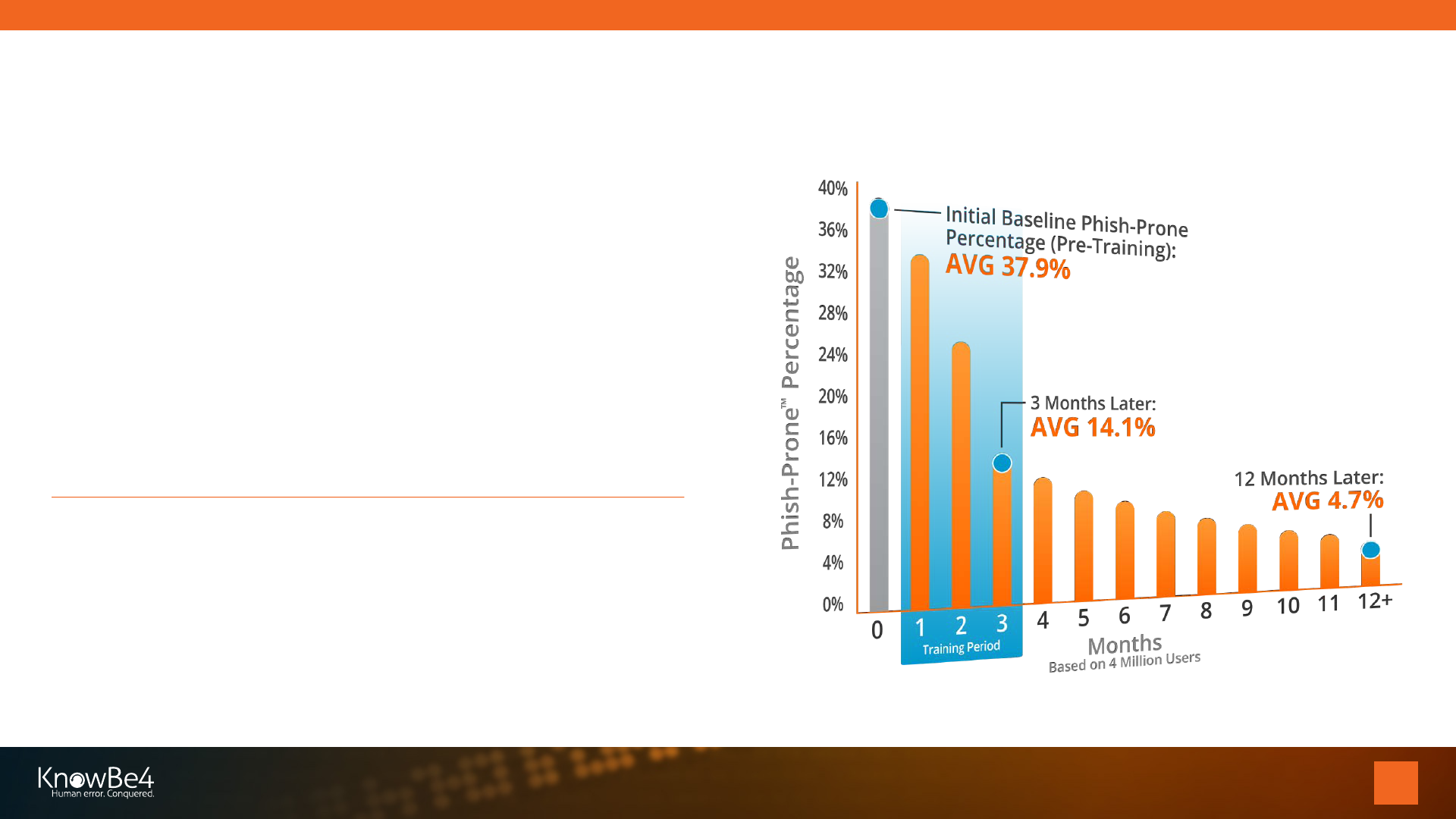
Generating Industry-Leading Results and ROI
5
• Reduced Malware Infections
• Reduced Data Loss
• Reduced Potential Cyber-theft
• Increased User Productivity
• Users Have Security Top of Mind
87% Average Improvement
Across all industries and sizes from baseline testing to one
year or more of ongoing training and testing
Note: The initial Phish-Prone percentage is calculated on the basis of all users evaluated. These users had not
received any training with the KnowBe4 platform prior to the evaluation. Subsequent time periods reflect
Phish-Prone percentages for the subset of users who received training with the KnowBe4 platform.
Source: 2020 KnowBe4 Phishing by Industry Benchmarking Report

Questions?
Tel: 855-KNOWBE4 (566-9234) | www.KnowBe4.com | Sal[email protected]
Roger A. Grimes– Data-Driven Defense Evangelist, KnowBe4
Twitter: @rogeragrimes
https://www.linkedin.com/in/rogeragrimes/