
© 2021 Cisco and/or its affiliates. All rights reserved. Page 1 of 51
Multiple Cisco DNA Center
to
Single Cisco ISE
Prescriptive Deployment Guide
November 2021
First Publish: October 2021
Last Update: November 2021
Prescriptive Deployment Guide
Cisco Public

© 2021 Cisco and/or its affiliates. All rights reserved. Page 2 of 51
Contents
Hardware and Software Version Summary ...................................................................................................................... 3
About This Guide .............................................................................................................................................................. 3
Define................................................................................................................................................................................ 5
Design ............................................................................................................................................................................... 7
Deploy ............................................................................................................................................................................. 13
Process 1: Request Package and Installation ................................................................................................................. 13
Process 2: Integrate Multiple Cisco DNA Center with Single Cisco ISE .......................................................................... 15
Operate ........................................................................................................................................................................... 42
Appendix A: Hardware and Software Versions .............................................................................................................. 49
Appendix B: References Used in this Guide ................................................................................................................... 50
Feedback ......................................................................................................................................................................... 51
© 2021 Cisco and/or its affiliates. All rights reserved. Page 3 of 51
Hardware and Software Version Summary
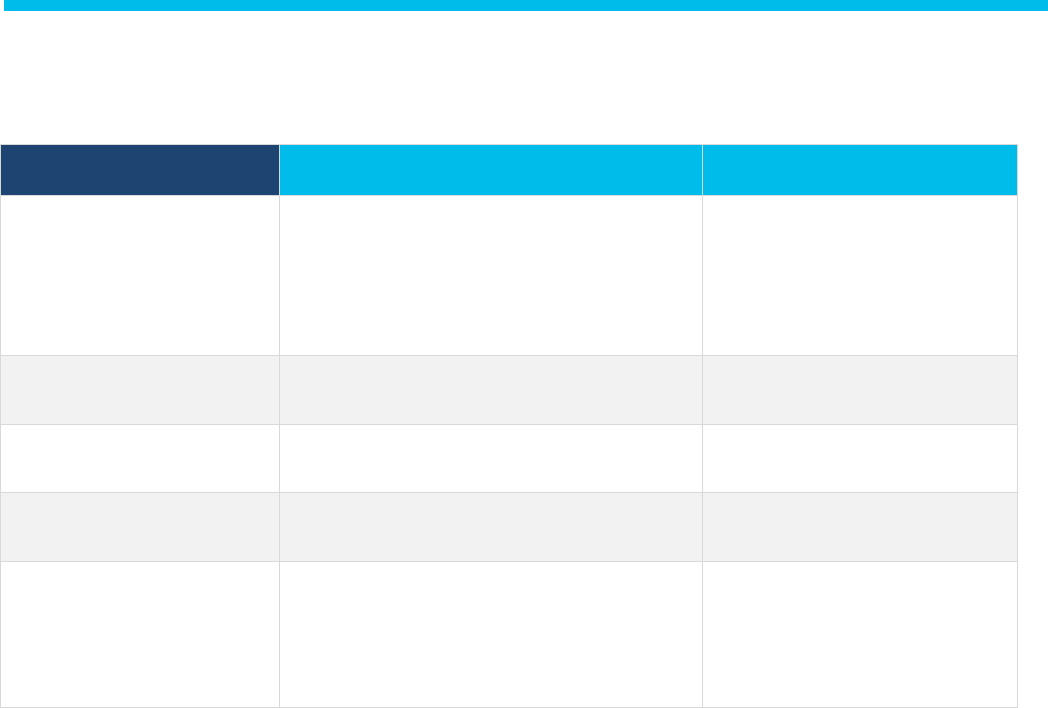
Table 1. Hardware and Software Version Summary
Item
Part number
Minimum Software version
Cisco® DNA Center Appliance
1
●
DN1-HW-APL (M4-based chassis)
●
DN2-HW-APL (M5-based chassis)
●
DN2-HW-APL-L (M5-based chassis)
●
DN2-HW-APL-XL (M5-based chassis)
1.3.3.5 or higher
SD Access Package
2
●
sd-access
3
See Cisco DNA Center Release Notes for
applicable version
Access Control Application Package
2
●
access-control-application
3
See Cisco DNA Center Release Notes for
applicable version
Multiple Cisco DNA Center Package
2
●
multi-dnac-enablement
3
See Cisco DNA Center Release Notes for
applicable version
Cisco Identity Services Engine
●
All supported Cisco Secure Network Server (SNS)
Appliances
●
R-ISE-VMM-K9=
ISE 2.4 Patch 11 or higher
ISE 2.6 Patch 3 or higher
ISE 2.7 Patch 1 or higher
ISE 3.0 – All Patches
1
Deployments supported:
●
Single Node Cluster
●
Single Node Cluster with Disaster Recovery (DR)
●
3-Node High Availability Cluster
●
3-Node High Availability Cluster with Disaster Recovery
2
GUI Display Name
3
CLI Display Name

© 2021 Cisco and/or its affiliates. All rights reserved. Page 4 of 51
About This Guide
This guide provides technical guidance to design, deploy and operate the Software-Defined Access Solution using Multiple Cisco
DNA Center Clusters with a single Cisco Identity Service Engine (ISE) deployment. It focuses on the steps to integrate these
multiple Cisco DNA Center clusters with a single Cisco ISE system.
This guide contains four major sections:
The DEFINE section defines the use cases for the Multiple Cisco DNA Center to ISE feature and its benefits in Cisco Software-
Defined Access (SD-Access) Fabric.
The DESIGN section shows the deployment topology, solution overview, requirements, and considerations with Multiple Cisco
DNA Center to ISE solution.
The DEPLOY section demonstrates the steps involved to enable Multiple Cisco DNA Center to ISE feature.
The OPERATE section demonstrates the Day N procedure and basic troubleshooting tips to be followed on Cisco DNA Center
Clusters and Cisco ISE with respect to Multiple Cisco DNA Center Feature.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 5 of 51
Define
Cisco DNA Center and Cisco Identity Service Engine integrates to solve multiple use cases such as Micro-Segmentation, secured
network access for authorized users, guests, and onboarding IoT devices into a Software Defined Access network. Cisco SD-
Access customers with Large or Distributed Enterprise Fabric networks often leverage more than one Cisco DNA Center cluster
for management simplicity, multi-regional deployments and even for compliance reasons. At the same time, they leverage a
single Cisco ISE cluster for globally consistent Group-based Access Control Policy. The "Multiple Cisco DNA Center” feature
centrally manages Virtual Networks, Scalable Groups, Group-based Access Control Policy, Access Contracts and Virtual Networks
to Scalable Group associations. It does so by allowing multiple Cisco DNA Center clusters to integrate with a single Cisco ISE
system.
What is covered in this Guide?
This guide provides guidance to Cisco Software-Defined Access customers integrating Multiple Cisco DNA Center clusters with
Cisco ISE. The process, procedure, and steps listed in this guide are working configurations verified with the Cisco DNA Center,
Cisco ISE, and Cisco IOS XE code versions listed in Appendix A.
What is NOT covered in this Guide?
Although this deployment guide is about Cisco DNA Center and Cisco ISE, it does not cover the initial bootstrap and installation
of the Cisco DNA Center appliances and Cisco ISE deployment, shared services installation and deployment such as DHCP, DNS,
and network connectivity configuration between various infrastructure components such as the routers and switches.
Deployment of the SD-Access Fabric and its various features are beyond the scope of this guide as well.
For more information on these items, please see additional references in Appendix B.
About Cisco DNA Center and SD-Access
Cisco DNA Center is the network management and command center for the Cisco Digital Network Architecture (DNA), built on
intent-based networking principles. It helps you build the new network and deliver better experiences more securely, so you
can focus on your business, and not on your network. It creates a holistic end-to-end platform for your enterprise so you can
better manage the business. Cisco DNA Center provides a centralized management dashboard for complete control of this new
network. This platform can simplify IT network operations, proactively manage the network, provide consistent wired and
wireless policy, and correlate insights with contextual cognitive analytics.
Cisco DNA Center is a hardware appliance powered through a software collection of applications, processes, services, packages,
and tools. This software provides full automation capabilities to deploy networks in minutes, to perform device upgrades and
patches network-wide with a minimal clicks, and to help ensure configuration consistency and save your team time. It also
provides visibility and network assurance through intelligent analytics combined with AI/ML which has more than 30 years of
best practices to help optimize your network's performance, reduce troubleshooting time for your team, and lower the cost of
network operations.
Cisco® Software-Defined Access (SD-Access) is the industry’s first intent-based networking solution for the Enterprise built on
the principles of Cisco’s Digital Network Architecture (Cisco DNA). Cisco SD-Access provides automated end-to-end
segmentation to separate user, device and application traffic without redesigning the network. Cisco SD-Access automates user
access policy so organizations can make sure the right policies are established for any user or device with any application across
the network. This is accomplished with a single network fabric across LAN and WLAN which creates a consistent user experience
anywhere without compromising on security.
Building this next-generation solution involved some key foundational elements including:
Controller-based orchestrator to drive business intent into the orchestration and operation of network elements including day-
0 configuration of devices and policies associated with users, devices and endpoints as they connect to a network.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 6 of 51
Network fabric leveraging Virtual Network (VN) overlays in order to support mobility, segmentation and programmability at a
very large scale.
Programmable switches to build a modern infrastructure for automated device provisioning, open API interfaces, granular
visibility using telemetry capabilities along with seamless software upgrades.
Companion Resources
Find the companion guides Cisco Software-Defined Access Solution Design Guide CVD, Cisco DNA Center & ISE Management
Infrastructure Deployment Guide, SD-Access Fabric Provisioning Prescriptive Deployment Guide, SD-Access for Distributed
Campus Prescriptive Deployment Guide, related deployment guides, design guides, and white papers, at the following pages:
●
https://www.cisco.com/go/designzone
●
https://cs.co/en-cvds
●
https://cs.co/sda-resources
If you didn’t download this guide from Cisco Community or Design Zone, you can check here for the latest version of this guide.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 7 of 51
Design
Deployment Topology Overview
Solution Overview
Cisco DNA Center provides a mechanism to create a trusted communications link with Cisco ISE to propagate Virtual Networks
(VNs), Scalable Group Tags (SGTs), Access Contracts, Group-Based Access Control (GBAC) Policy, and VN-to-SGT Associations.
Here, ISE is the consumes of this information. Cisco ISE provides the runtime policy services to the network, which includes
Group-Based Access Control Policy downloads to the network devices.
The Multiple Cisco DNA Center feature leverages the existing secure connection with Cisco ISE to replicate VNs, SGTs, Access
Contracts, GBAC Policy, and VN-to-SGT Associations from one cluster to another cluster which are integrated with same Cisco
ISE deployment. Here, ISE takes this information learned from one cluster (the Author Node as defined below) and propagates it
to the other clusters (Reader Nodes).
Multiple Cisco DNA Center feature is supported on all appliance types (44-core, 56-core, and 112-core) deployed in as either a
single-node cluster or a three-node cluster with or without Cisco DNA Center Disaster Recover enabled.
Solution Components
The Multiple Cisco DNA Center feature has specific role designations for the clusters:
●
Author Node Cluster
●
Reader Node Cluster

© 2021 Cisco and/or its affiliates. All rights reserved. Page 8 of 51
Author Node Cluster
This is the first cluster that integrates with the ISE deployment. The Author Node cluster is the source of truth for all of Cisco SD-
Access policy information. The Author Node cluster manages VNs, SGTs, Access Contracts, GBAC Policy, and VN-to-SGT
Associations. Creation, modification, or deletion of policy components can only be performed on the Author Node cluster.
The Author Node cluster pushes VN and policy related information to ISE via ERS/PxGRID REST APIs for Cisco ISE to consume the
information and publishes it to all other Cisco DNA Center Clusters in the Reader Node role.
Only ONE (1) cluster can be designated as the Author Node supported. It is the only node that can be Brownfield (containing
user-defined Virtual Network, Scalable Groups (SGT’s), Access Contracts, Group-Based Access Control (GBAC) Policy and VN to
SGT Associations) Cisco DNA Center Cluster
Reader Node Cluster
All other Cisco DNA Center clusters are Reader Node cluster. Reader Node clusters have a Read-Only view of VNs, SGTs, Access
Contracts, GBAC Policy, and VN-to-SGT Associations. However, these objects are available to use for provisioning operations just
as if this were a stand-alone Cisco DNA Center cluster.
A Reader Node cluster does not display Access Contracts or Policies, though has a hyperlink to cross-launch to the Author Node
cluster to access that information. Reader Node clusters will consume the same VNs, SGTs, Access Contracts, GBAC Policy, and
VN-to-SGT associations that are defined on the Author Node cluster.
VNs can only be created on the Author Node cluster. Once created they are propagated to the Reader Node clusters. To use this
VN on the Reader Node clusters, the VN must be added to the fabric site. The Reader Node clusters will configure the associated
network attributed such as Virtual Network Identifies (VNID), Route Targets (RT), and Route Distinguishers (RD) which are local
to that cluster.
Except for the VN and Policy features listed above, each Reader Node cluster are independent clusters that manage their own
network infrastructure.
The Multiple Cisco DNA Center feature enables global policy administration across multiple Cisco DNA Center clusters integrated
to a single Cisco ISE. This capability does not change the underlying limitations of managing virtual networks and fabrics on
multiple Cisco DNA Center clusters. A virtual network may have the same name across multiple Cisco DNA Center clusters, which
allows it to support consistent security group-virtual network associations across multiple clusters. But at the individual cluster
level, the actual network attributes to associate with a VN (VRF, route target, route distinguisher, and so on) are not identical
across clusters. This is the same as when operating independent Cisco DNA Center clusters.
Before adding a Cisco DNA Center node as a Reader, you must remove all admin-created Cisco SD-Access policy data on the
Reader Node cluster for Cisco DNA Center to integrate with Cisco ISE. This includes non-default Virtual Networks (any Virtual
Networks other than DEFAULT_VN and INFRA_VN), Scalable Group to VN mappings, User-defined Access Contracts and Group-
Based Access Control Policy.
Tech tip
In Cisco DNA Center Releases 2.2.2.x and earlier, up to THREE (3) Reader Node clusters are supported. This is FOUR (4) clusters in total
including the Author Node cluster.
In Cisco DNA Center Release 2.2.3.x and later up to FOUR (4) Reader Node clusters are supported. This is FIVE (5) clusters in total including
the Author Node cluster.
Accessing the Multiple Cisco DNA Center Cluster Software Package
The Multiple Cisco DNA Center functionality is not available as a General Availability feature. A Limited Availability package
called Multiple Cisco DNA Center is available only to approved customers. To get access to this software package, please reach

© 2021 Cisco and/or its affiliates. All rights reserved. Page 9 of 51
out to your Cisco Sales representative or Channel Partner to do a High-Level Design review. Upon design review approval, the
software package is released via the Cloud Catalog Server update, and the cluster administrator can download and install the
package. For Air-Gapped environment, packages will be released in a separate method for the cluster administrator to download
and install the respective package.
All Cisco DNA Center clusters that are integrated with the single Cisco ISE deployment must install this package. Once
downloaded, the package installation process automatically restarts the applicable services in the cluster. This installation and
service restart may take up to 10 minutes. Once the package is installed, a separate submenu is added under ☰ > System >
Settings > System Configuration > Multiple Cisco DNA Center Settings.
Cisco Multiple DNA Center Considerations
●
In Cisco DNA Center Releases 2.2.2.x and earlier, up to THREE (3) Reader Node clusters are supported. This is FOUR (4)
clusters in total including the Author Node cluster.
●
In Cisco DNA Center Release 2.2.3.x and later up to FOUR (4) Reader Node clusters are supported. This is FIVE (5) clusters
in total including the Author Node cluster.
●
Before adding Reader Node cluster, you must remove all user-defined Cisco SD-Access policy elements in order to
integrate with Cisco ISE. These include any user-defined VNs, SGTs, Access Contracts, and GBAC Policy.
●
Once the Multiple Cisco DNA Center Package is installed, the functionality is enabled in the cluster. Uninstalling the
package does not disable the functionality nor removes “Establishing Multi DNA Center environment” step with ISE
integration process.
●
VNs, SGTs, Access Contracts, GBAC Policy, and VN-to-SGT Associations can only be managed on the Author Node cluster.
Virtual Networks and SGTs are Read-Only on Reader Node clusters.
●
The ability to designate a Virtual Network as a Guest VN is not supported. This limitation is removed if using Cisco DNA
Center 2.2.3.x along with Cisco ISE 3.1.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 10 of 51
●
SGT to VN associations can only be managed on the Author Node cluster. These associations are available as Read-Only
on Reader Node clusters.
●
When a Cisco DNA Center cluster is upgraded, a new Multiple Cisco DNA Center package may be available. However, this
package is not automatically available for download. Use the earlier process to receive access to newly available packages
after upgrade.
●
After cluster upgrade, the existing Multiple Cisco DNA Center functionality will continue. If upgrading from 1.3.3.x to
2.x.x.x, ensure that the newer package is installed to avoid seeing potential issues in Multiple Cisco DNA Center settings
page. Additional fixes or capabilities are made available through the SD-Access, Access Control Application, and Cisco
DNA Center UI packages. The standard cluster upgrade process should automatically download and install these
packages. Please consult the Cisco DNA Center Release Notes for specific package version numbering for a given release.
●
The user-defined pxGrid Subscriber name under ☰ > System > Settings > Authentication and Policy Servers across all
FIVE Cisco DNA Center must be unique. This is applicable only if you are running Cisco DNA Center versions 1.3.3.x and
below. The Subscriber Name is auto-generated starting with Cisco DNA Center version 2.1.1.x and later.
●
The ability to associate a vManage VPN to a Virtual Network is not supported. This limitation is removed if using Cisco
DNA Center 2.2.3.x along with Cisco ISE 3.1.
●
When promoting a Reader Node cluster to the Author Node role, the application names for specific Access Contracts
found under ☰ > Policy > Group-Based Access Control > Access Contracts are not populated. The application names are
displayed as Advanced. TCP/UDP port numbers are populated. Please note, the behavior of the network is unchanged
since these SGACLs in ISE have not changed. To populate the names, review all the Access Contracts after a promotion
operation and edit them selecting the application name.
Multiple Cisco DNA Center to ISE Scale Information
Table 2. Multiple Cisco DNA Center VN and IP Pool Scale
Cisco DNA Center 1.3.3.x
ISE 2.4 Patch 14 and later
ISE 2.6 Patch 8 and later
ISE 2.7 Patch 3 and later
ISE 3.0 Patch 2 and later
300 Virtual Networks
1250 IP Pools (Total)
Cisco DNA Center 1.3.3.x
ISE 2.4 Patch 13 and earlier
ISE 2.6 Patch 7 and earlier
ISE 2.7 Patch 2 and earlier
ISE 3.0 Patch 1 and earlier
100 Virtual Networks
600 IP Pools (Total)

© 2021 Cisco and/or its affiliates. All rights reserved. Page 11 of 51
Table 3. Multiple Cisco DNA Center VN and VLAN Name Scale
Cisco DNA Center 2.1.1.x
ISE 2.4 Patch 14 and later
ISE 2.6 Patch 8 and later
ISE 2.7 Patch 3 and later
ISE 3.0 Patch 2 and later
300 Virtual Networks
1250 VLAN Names (Total)
Cisco DNA Center 2.1.1.x
ISE 2.4 Patch 13 and earlier
ISE 2.6 Patch 7 and earlier
ISE 2.7 Patch 2 and earlier
ISE 3.0 Patch 1 and earlier
100 Virtual Networks
600 VLAN Names (Total)
Tech tip
A VLAN Name is configured in the Fabric Site – Host Onboarding screen. The configuration allows an administrator to have a single VLAN
Name (for use in authorization profiles and authorization policies in Cisco ISE) for multiple IP pools. A common use case is to have a single
VLAN Name for a specific virtual network across all sites (where every site has one or more unique IP pools).
Multiple DNA Center Latency Requirements
The latency requirements for this feature are unchanged from the standard latency requirements. Please refer to the SD-Access
requirements section on the Cisco DNA Center datasheet for latency information.
Cisco Multiple DNA Center Policy Management
Cisco DNA Center 1.3.1.x software release introduced the Access Control Application (ACA) package with which Scalable Group,
Access Contracts and Group-Based Access Control Policy are available on the Cisco DNA Center user interface. Once Cisco DNA
Center was integrated with Cisco ISE and Policy Migration was performed and synchronized, policy authoring privileges are be
handled within Cisco DNA Center and ISE becomes Read-Only.
Usually, the policy data on Cisco DNA Center and Cisco ISE is consistent, so no special handling or conversion of data is
necessary. In case of minor discrepancies or inconsistencies or if there is a conflict, the data in Cisco ISE is given precedence, so
as not to introduce changes in policy behavior in the network. For Conflict resolution and actions to take during migration,
please see Group-Based Access Control: Policy Data Migration and Synchronization in the Cisco DNA Center user guide
To retain the policy (Scalable Groups, Access Contracts and Group-Based Access Control Policy) authoring function on Cisco ISE,
either:
●
Skip the Data migration and Synchronization step under ☰ > Policy > Group-Based Access Control > Policies.
●
Navigate to ☰ > Policy > Group-Based Access Control > Policies > GBAC Configuration. and select Manage Group-Based
Access Control in ISE, GBAC UI in Cisco DNA Center will be inactive and click Save if data migration is complete.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 12 of 51
Cisco Multiple DNA Center Upgrade Recommendations
In a Cisco Multiple DNA Center environment, it’s strongly recommended to run the same Cisco DNA Center software version
and packages across all Author and Reader Node clusters. The exception to this is during the process of cluster upgrades.
Tech tip
Basic functionality of the Multiple DNA Center feature does not require the same software version of all the participating Author and
Reader Node Cluster. However, using mismatched code versions will result in a difference in fixes, capabilities, and features between the
clusters. The same Cisco DNA Center software version and packages is strongly recommended across all Author and Reader Node clusters.
Upgrade all Reader Node clusters first, and then upgrade the Author Node cluster to avoid feature disparity and feature
incompatibility across versions. Avoid promotion of a Reader Node cluster to the Author Node role in the middle of an upgrade
cycle. All Cisco DNA Center clusters should be upgraded and running the same version software version before promoting a
Reader Node Cluster.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 13 of 51
Deploy
This section focuses on deployment guidelines with various workflows including the Multiple Cisco DNA Center Package
installation and Policy Authoring.
There are two implementation options available when it comes for the Multiple Cisco DNA Center to ISE deployment
●
A new deployment of multiple Cisco DNA Center clusters that are not currently integrated with ISE.
●
An existing Cisco DNA Center cluster that is integrated with ISE and new DNA Center Clusters with or without Cisco ISE
Integration.
This prescriptive deployment guide addressed the second option as the majority of customers start with Single Cisco DNA Center
and add additional clusters.
Process 1: Request Package and Installation
The multiple Cisco DNA Center cluster functionality isn’t currently available in the Cisco DNA Center software release for General
Availability. A Limited Availability package (Multiple Cisco DNA Center) is available only to approved customers.
Download/Install Multiple Cisco DNA Center Package
Step 1. Connect with your Cisco Sales Representative or Channel Partner for:
●
High-Level Design review
●
Multiple Cisco DNA Center Package release
Packages will be released to the Cisco DNA Center Cluster via Cloud catalog server update. Expect the packages to be available in
1 or 2 days.
Step 2. Navigate to ☰ > System > Software updates to first download the package and install the package.
Tech tip
The package installation process automatically restarts affected services in Cisco DNA Center, which may take up to 10 minutes.
Step 3. To verify the Package installation, Navigate to ☰ > System > Software Updates > Installed Apps.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 14 of 51
Tech tip
After the required information is provided, Cisco DNA Center retries the Integration process and integration status is shown on the side
panel display. Packages highlighted in green are supporting applications required for Multiple Cisco DNAC Center feature to work. All Cisco
DNA Center clusters that you intend to integrate into a single Cisco ISE deployment must install this package.
Step 4. Navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center Settings to verify the default
role of the cluster
With the Multiple Cisco DNA Center Package installed, the cluster, by default, is shown as the Author Node cluster as shown in
Figure 5 below. Upon integrating (first1st time) or reintegrating (already integrated without package) with Cisco ISE, role
negotiation happens, and the first Cisco DNA Cluster will resume the role of Author Node cluster and subsequent Cisco DNA
Cluster will become the role of Reader Node clusters.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 15 of 51
Process 2: Integrate Multiple Cisco DNA Center with Single Cisco ISE
Integrate / Reintegrate Cisco DNA Center with Cisco ISE
For Greenfield deployments, prerequisites must be met on both Cisco DNA Center and ISE prior to the integration. Please refer
to Cisco DNA Center and Cisco ISE Integration section in the Cisco DNA Center Administrator Guide for more information.
For Brownfield environments wherein Cisco DNA Center is already integrated with ISE, follow the steps below to reintegrate
Cisco DNA Center and Cisco ISE using the Multiple Cisco DNA Center Package. This allows Cisco DNA Center to negotiate the
Author or Reader Node cluster role based on if it the first cluster or subsequent cluster joining ISE with Multiple Cisco DNA
Center Package.
Step 1. In Cisco DNA Center, navigate to ☰ > System > Settings> External Services> Authentication and Policy Servers
Step 2. Hover over … under the Action column and select Edit to reenter the Cisco ISE Super Admin password.
Tech tip
After the required information is provided, Cisco DNA Center retries the Integration process, and the integration status is shown on the side
panel display.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 16 of 51

© 2021 Cisco and/or its affiliates. All rights reserved. Page 17 of 51
Tech tip
This is a five-step reintegration process, and the fourth step, which is circled above, is where Cisco DNA Center negotiates the
Author/Reader Node role with ISE.
Step 3. Close the side panel and ensure the Authentication and Policy Server page shows Status as ACTIVE.
Tech tip
If the status of the configured Cisco ISE server is “FAILED” due to password change, click Retry, and update the password to resynchronize
with ISE.
Step 4. Navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center Settings to verify the
negotiated role of the cluster as Author Node.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 18 of 51
Step 5. Navigate to ☰ > Policy > Virtual Network to confirm Read-Write (edit) privileges for Virtual Network.
© 2021 Cisco and/or its affiliates. All rights reserved. Page 19 of 51
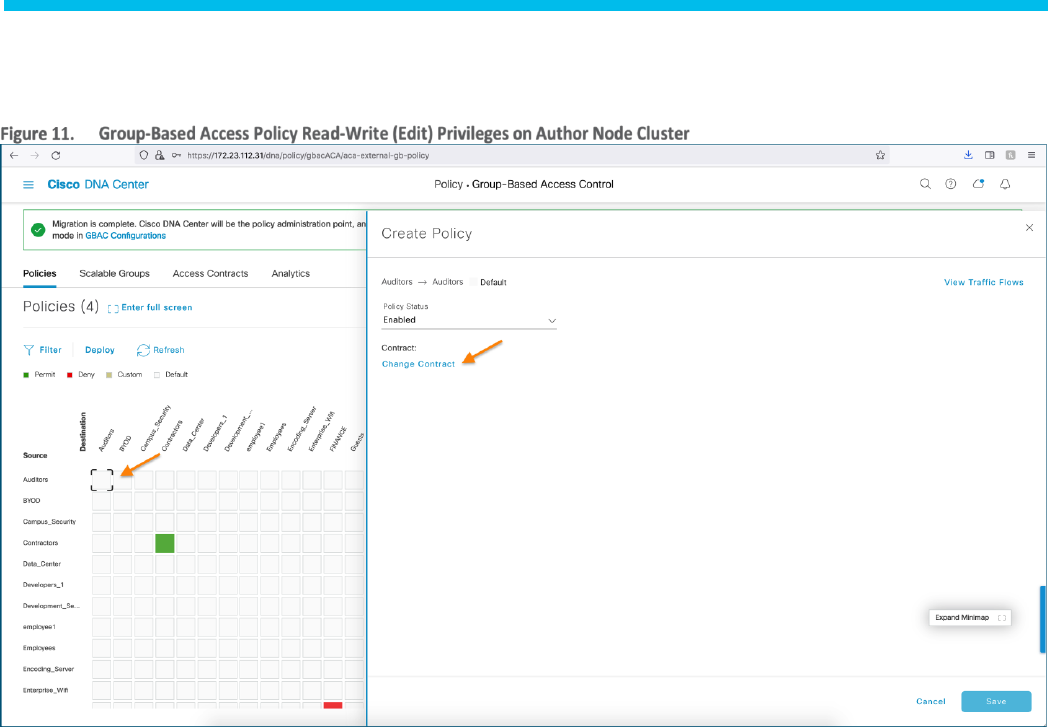
Step 6. Navigate to ☰ > Policy > Group-Based Access Control > Policies to view the Group-Based Access Control Policy Matrix
and to confirm Read-Write (edit) privileges of the Matrix.
Step 7. Navigate to ☰ > Policy > Group-Based Access Control > Scalable Groups to view the total number of Scalable Groups
and to confirm Read-Write (edit) privileges.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 20 of 51
Integrating other Cisco DNA Center Clusters with Cisco ISE as Reader Nodes
To integrate subsequent Cisco DNA Center clusters using the Multiple Cisco DNA Center Package to same Cisco ISE, the cluster
must be in a Greenfield-state. This means that it cannot have:
●
Non-Default Virtual Networks—Any Virtual Networks other than DEFAULT_VN and INFRA_VN.
●
Non-Default Scalable Groups—Any Security Group other than those with a tag value 0 to 15(0xf)
●
Non default Virtual Network to Scalable Group mappings— All 15 SGT will be mapped to DEFAULT_VN
●
Non-Default Scalable Groups (Security Groups)
Each user-defined (non-default) constructs described above must be removed or Cisco DNA Center displays a banner, the
connection is refused, and the integration does not complete.
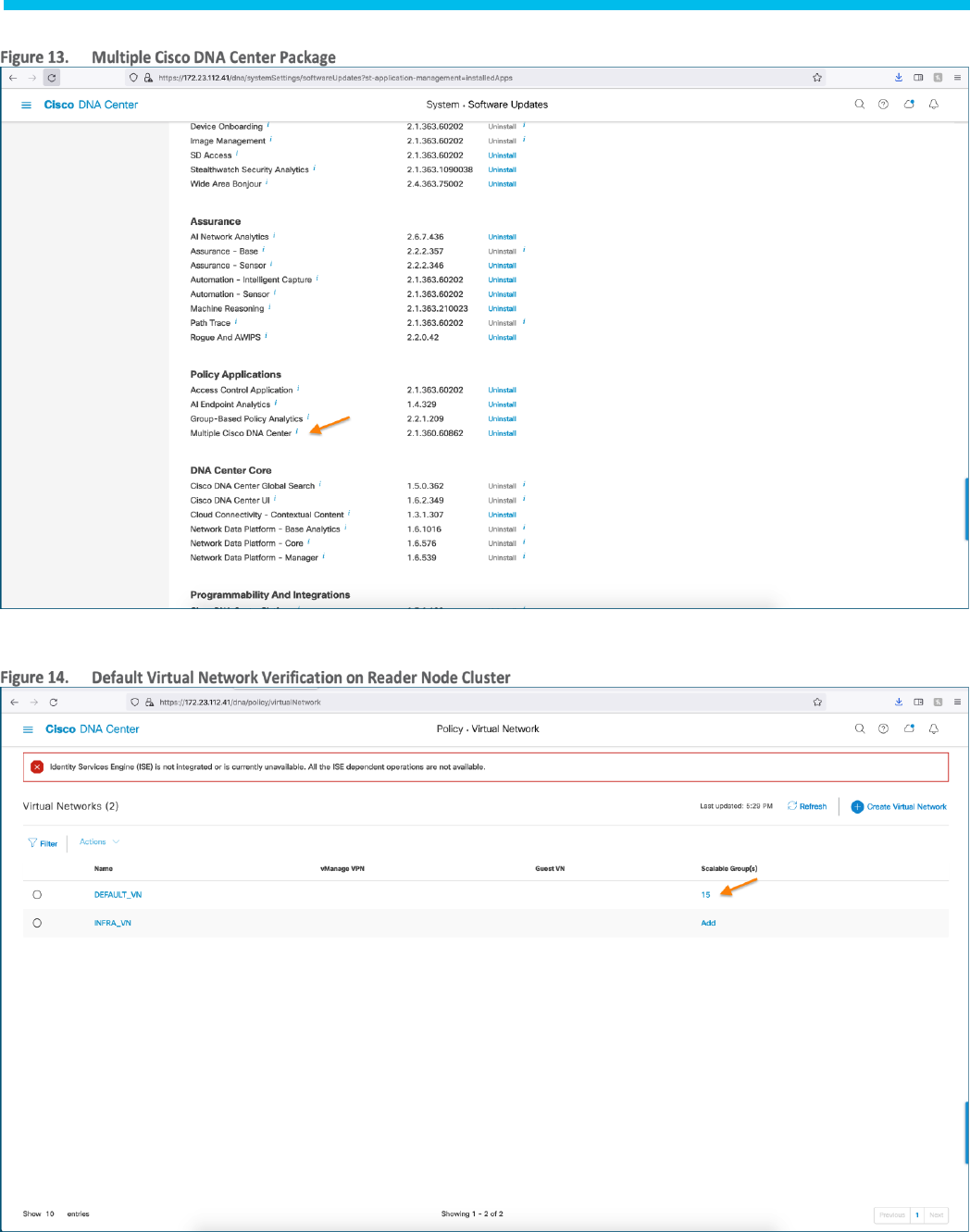
Step 1. Verify the Package installation by navigating to ☰ > System > Software Updates > Installed App
© 2021 Cisco and/or its affiliates. All rights reserved. Page 21 of 51
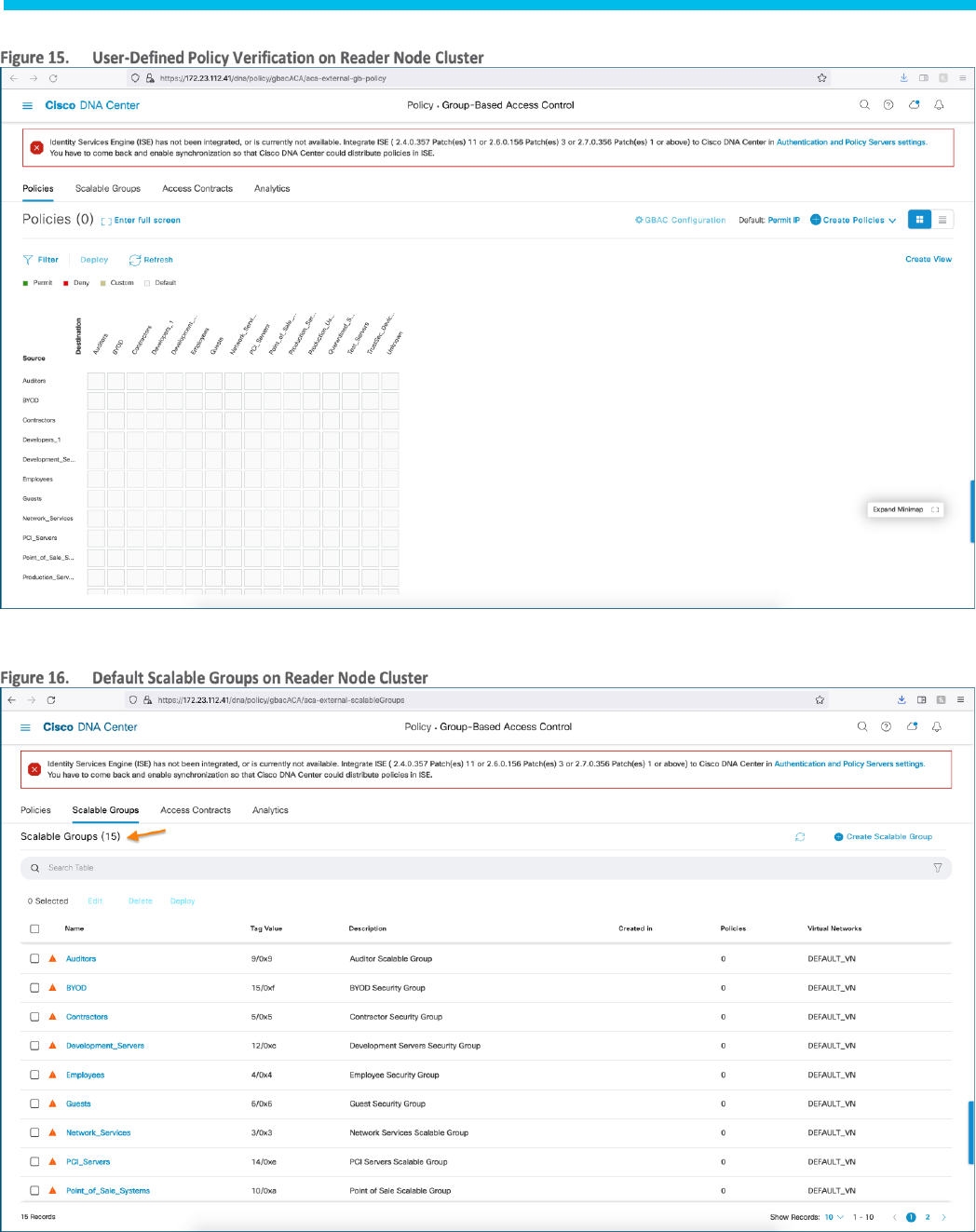
Step 2. Navigate to ☰ > Policy > Virtual Network to verify cluster includes only the default Virtual network.
Step 3. Navigate to ☰ > Policy > Group-Based Access Control to verify that there are no user-defined policies.
© 2021 Cisco and/or its affiliates. All rights reserved. Page 22 of 51
Step 4. Navigate to ☰ > Policy > Scalable Groups to verify non-user-defined Scalable Groups.
Step 5. In the Cisco DNAC Center GUI, Click the Menu icon ☰ > System > Settings> External Services> Authentication and
Policy Servers,

© 2021 Cisco and/or its affiliates. All rights reserved. Page 23 of 51
Step 6. Click Add.
Step 7. Select ISE.
Step 8. Configure the Primary AAA Server by providing the following information:
• Server IP address: Primary PAN IP Address
• Shared Secret: Key for device authentications
• Username: Name that is used to login to the Cisco ISE CLI/GUI (Must be Super Admin)
• Password: Password for the Cisco ISE CLI/GUI username
• FQDN: Fully qualified domain name (FQDN) of the Cisco ISE Server
• Virtual IP Address[optional]: Virtual IP address of the load balancer
• Toggle Advanced Settings button and configure Protocol: TACACS and RADIUS
Step 9. Click Add.
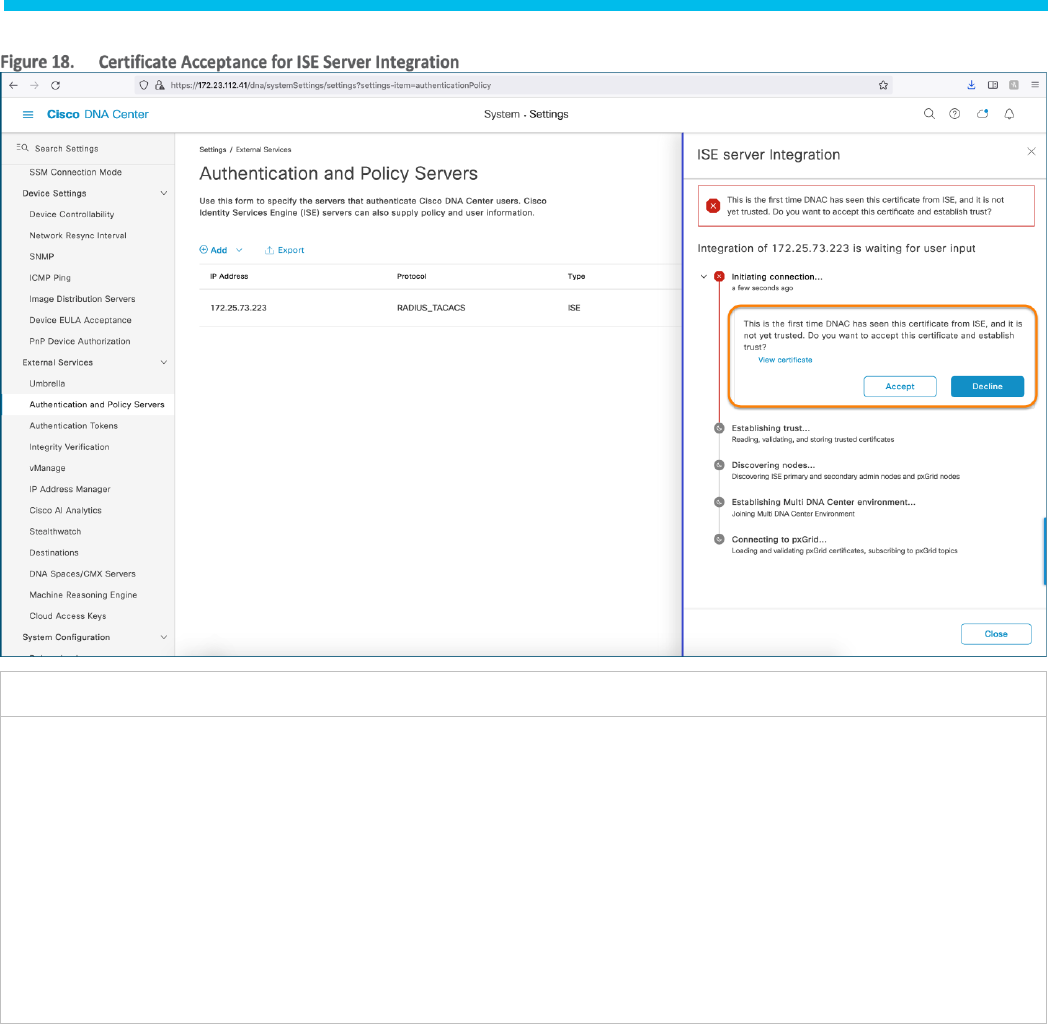
Step 10. In the side panel, due to first-time Integration, click on the ACCEPT button for Cisco DNA Center to accept the
Certificate pushed by Cisco ISE.
© 2021 Cisco and/or its affiliates. All rights reserved. Page 24 of 51
Tech tip
To automatically approve pxGrid client within ISE:
●
Navigate to Administration > pxGrid Services > Settings.
●
Click the checkbox next to 🗹 Automatically approve new certificate-based accounts.
●
Click Save.
To manually approve a pxGrid Client within ISE:
●
Navigate to Administration > pxGrid Services > All Clients.
●
Click Total Pending Approval(x).
●
Click Approve All.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 25 of 51
Tech tip
This is a five-step reintegration process, and the fourth step, which is circled above, is where Cisco DNA Center negotiates the
Author/Reader Node role with ISE.
Step 11. Close the Side Panel window and make sure the Authentication and Policy Server page shows Status as ACTIVE.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 26 of 51
Step 12. Navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center Settings to verify the Reader
& Author Role.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 27 of 51
Step 13. Navigate to ☰ > Policy > Virtual Network to confirm Virtual Networks have been synchronized from Author Node
cluster and that privileges are Read-Only. This is shown in the figure below by the grey-out option to select the Virtual Network.
Step 14. Navigate to ☰ > Policy > Group-Based Access Control > Policies to confirm the Reader Node cluster has a hyperlink to
cross-launch to the Author Node cluster for Policy-Information authoring as shown in Figure 23.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 28 of 51
Step 15. Navigate to ☰ > Policy > Group-Based Access Control > Scalable Groups to confirm Scalable Groups synchronized
from the Author Node cluster and that privileges are Read-Only.
Step 16. Navigate to ☰ > Policy > Group-Based Access Control > Access Contracts to confirm the Reader Node cluster has a
hyperlink to cross-launch to the Author Node cluster for Access-Contract authoring as shown in Figure 24.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 29 of 51
Step 17. On the Author Node cluster, navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center
Settings to verify the Author Node and Reader Node roles.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 30 of 51
Configuring Virtual Networks
Configuring, modifying, or deleting Scalable Groups, Access Contracts, Group-Based Access Control Policies, and Virtual
Networks is only possible on the Author Node cluster.
Perform the below steps to first create Virtual Network
Step 1. In the Cisco DNA Center GUI, navigate to ☰ > Policy > Virtual Network.
Step 2. Click Create Virtual Network, and the Create Virtual Network slide-in pane appears.
Step 3. In the Name field, enter the name of the Virtual Network.
Step 4. [Optional] Select the 🗹 Guest Virtual Network check box to configure the virtual network as a guest network.
Tech tip
If using Cisco DNA Center release 2.2.3.x along with ISE 3.1, the Guest Virtual Network attribute, which is enabled by selecting the 🗹 Guest
Virtual Network, is shared to Reader Node clusters. In any other combination of Cisco DNA Center release along with ISE release, the
ability to designate a Virtual Network as a Guest VN is not supported.
Step 5. Click Save.
Step 6. On the Author Node clusters, navigate to ☰ > Policy > Virtual Network to verify the Virtual Network creation and
Read-Write privileges as show in Figure 27 below. Note that the radio buttons are not greyed out.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 31 of 51
Step 7. On the Reader Node clusters, navigate to ☰ > Policy > Virtual Network to verify the Virtual Network creation and
Read-Only privileges as show in Figure 28 below. Note that the radio buttons are greyed out.
Deleting a Virtual Network

© 2021 Cisco and/or its affiliates. All rights reserved. Page 32 of 51
Deleting a Virtual Network (VN) on the Author Node cluster requires prerequisite actions as the Author Node cluster is not
aware of the VN usage on Reader Node clusters.
●
All references to a VN on all the Reader Node clusters must be removed before attempting to delete that VN on the
Author Node cluster.
●
If a VN is deleted on the Author Node cluster, the VN is deleted on the Author Node cluster and the Reader Node clusters
no longer have a reference to it.
●
If a Reader Node cluster is using that VN, that VN displays as out of sync with Author.
In this occurs, perform the steps below to synchronize the Reader Node cluster with the Author Node cluster.
Step 1. Remove all the references of Virtual Network on the Reader Node cluster.
Step 2. Perform one of the actions below to resync:
On Author Node, navigate to ☰ > Policy > Group-Based Access Control > Policies > GBAC Configuration and click Re-
sync policy data now.
On the Reader Node cluster, navigate to ☰ > System > Settings> External Services> Authentication and Policy
Servers and re-enter the ISE Super Admin Password to perform a resynchronization with ISE.
Configure Scalable Groups and associate a Scalable Group to Virtual Network
Perform the below steps to create Scalable Groups and associate a Scalable Group to Virtual Network on the Author Node
cluster.
Step 1. In the Cisco DNA Center, navigate to ☰ > Policy > Group-Based Access Control > Scalable Groups
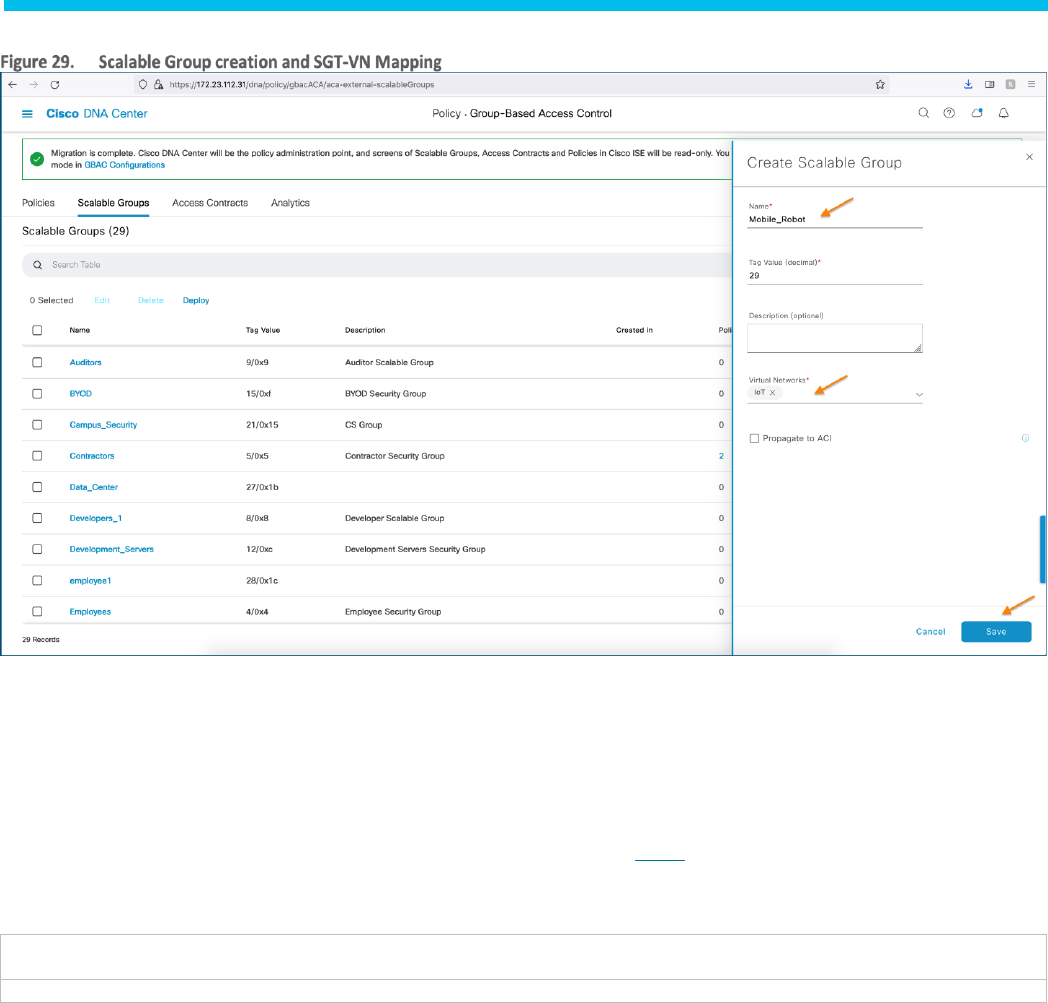
Step 2. Click Create Scalable Group, the Create Scalable Group slide-in pane appears.
Step 3. In the Create Scalable Group slide-in panel, enter a name and description for the Scalable Group.
Step 4. Remove the DEFAULT_VN Virtual Network by clicking the X symbol next to the name.
Step 5. From the drop-down, select the respective Virtual Network (e.g., IoT).
© 2021 Cisco and/or its affiliates. All rights reserved. Page 33 of 51
Step 6. Click Save.
The Scalable Groups window displays the Scalable Group name, tag value, assigned Virtual Networks and associated
policies.
Step 7. At the bottom right of the page, choose (Show Records) to show 25, 50, or 100 records per page to view all records.
An orange triangle icon is displayed next to the Scalable Group if synchronization with Cisco ISE is incomplete.
Step 8. To manually sync, Locate the name of Scalable Group as entered in Step 3 and select the Scalable Group by checking
the checkbox next to the name of the Scalable Group
Step 9. Click Deploy for Cisco DNA Center pushes the information to Cisco ISE via Rest API.
Tech tip
Once Deployed, the Sync not started / Sync in progress triangle will be removed.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 34 of 51
Step 10. On a Reader Node cluster, navigate to☰ > Policy > Group-Based Access Control > Scalable Groups to verify the
Scalable Group creation and association of a Scalable Group to Virtual Network.
Step 11. To show more than 10 records per page, click Show Records and select 10, 25, 50, or 100 to see the selected number
of Scalable Groups per page as shown in Figure 31.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 35 of 51
Deleting a Scalable Group
Deleting a Scalable Group on the Author Node cluster requires prerequisite actions. The Author Node cluster is not aware of
Scalable Group usage on a Reader Node cluster. You must remove all references to the security group on all the Reader Node
clusters before attempting to delete that security group on the Author Node cluster. If you delete a security group on the Author
Node cluster, that security group is deleted on the Author Node cluster, Cisco ISE and on the Reader Node cluster if there are no
references to it. If one of the Reader Node clusters is using that Security Group, that security group displays as out of sync with
Author.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 36 of 51
Perform the steps below to stay in sync with the Author Node cluster.
Step 1. Remove all the references of Scalable Group on the Reader Node cluster.
Step 2. Navigate to ☰ > System > Settings> External Services> Authentication and Policy Servers and re-enter the Cisco ISE
Super Admin Password to perform a resynchronization with ISE.
Creating Access Contracts
An Access Contract is a set of rules that control the type of network traffic that is allowed to pass between the source and
destination Scalable Group. Security Group Access Control Lists (SGACLs) in ISE are called Access Contracts in Cisco DNA Center.
Access Contracts define the actions (permit or deny) performed when the traffic matches a network application, protocol, and
port.
The steps to manage Access Contract is the same process on standalone Cisco DNA Center cluster or cluster participating in the
Multiple Cisco DNA Center feature. The distinction is that creating, editing, and deleting Access Contracts is permitted only on
the Author Node cluster, and Access Contracts are not visible on the Reader Node clusters. A hyperlink is displayed to cross-
launch to the Author Node cluster’s Access Contracts page.
Please refer to Create Access Contracts section in the Cisco DNA Center User Guide for Access Contract creation and conflict and
resolution in case of mismatch between Cisco DNA Center and Cisco ISE.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 37 of 51

© 2021 Cisco and/or its affiliates. All rights reserved. Page 38 of 51
Create Group-Based Access Control Policy
Scalable Groups and Access Contracts are the basic building blocks of an Access-Control Policy. While creating an Access-Control
Policy, Scalable Groups and Contracts that have created before can be used or new Scalable Group and Contracts can be
created.
If you want to specify the network resources that can be accessed from a specific source group, you can create an access control
policy with a single source group and single or multiple destination groups or you can create an access control policy with a
single destination and multiple source groups.
Creating an Access Control policy is the exact same process on Standalone Cisco DNA Center or Multiple Cisco DNAC Center
Cluster. Managing(creating/editing/deleting) Access Control policy is permitted only on the Author Node cluster and Access
Control policy are not even visible on the Reader Cisco DNAC Cluster node, rather a hyperlink is displayed to cross-launch to
Author Node cluster’s Access Control Policy page.
Perform the below steps to create Group-based Control policy on the Author Node
Step 1. On the Author Node Cluster, navigate to ☰ > Policy > Group-Based Access Control > Polices.
Step 2. Click Create Policies.
Step 3. To create an Access-Control Policy with a single source and single destination group, select Source to Destination(s)
from the drop-down.
Step 4. Click on the radio button next to source Scalable Group (for example: Mobile_Robot).
Step 5. Click Next
Step 6. Choose the destination Scalable Group (for example: Smart_Plug).
Step 7. Click Next
Step 8. Click the radio button next to desired Access Contract.
Step 9. Click Next
The Summary window lists the policy that you created based on the selected Scalable Groups and contracts.
Step 10. Click Save.
Step 11. Click Deploy for Cisco DNA Center pushes the Policy information to ISE.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 39 of 51
Step 12. To verify to policy creation in Cisco DNA Center, map the Cell intersecting the Source and Destination Scalable Group
for the policy that was configured previously in Step 2 as shown in Figure 36.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 40 of 51
Step 13. On Cisco ISE, Navigate to Work Centers > TrustSec > TrustSec Policy > Egress Policy > Matrix to verify the policy push
from Cisco DNA Center.
Tech tip
The Edit, Add, Clear, and Deploy buttons are greyed out on Cisco ISE because Cisco DNA center is managing TrustSec Policy. Therefore,
these items are Read-Only on ISE.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 41 of 51

© 2021 Cisco and/or its affiliates. All rights reserved. Page 42 of 51
Operate
Operate section begins with a discussion around promoting Reader Node cluster to Author Node cluster and circumstances
when to promote and best practices to follow before this promotion. The later part of the section will focus on the basic high-
level troubleshooting steps
As part of the Multiple Cisco DNA Center solution architecture where we have multiple Cisco DNA Center Clusters and only one
has a special role for being policy Author. There may be instances where the Administrator needs to promote a Reader Node
cluster to take over the role of Author Node cluster. This promotion should not be done unless:
• The Author Node cluster is taken out of service or is otherwise unavailable for an extended period.
• The Author Node cluster is permanently unavailable or unresponsive for an extended period, and Policy changes are
required.
Graceful Promotion of Reader to Author role
Multiple Cisco DNA Center architecture supports a manual process to promote Reader Cisco DNA Cluster to Author Role if the
administrator plans to take the Author Node cluster out of service. All Reader Node clusters, by default, have a Promote to
Author button. You can start promoting a Reader Node cluster to an Author Node while your current Author Node cluster is still
in operation. Do not start the promotion operation while the existing Author Node cluster is busy. For example, while
synchronizing policies with ISE. If the Author Node cluster is busy, the promotion operation is staggered until the Author node
completes current processing.
1) Upon Graceful promotion of a Reader Node cluster (Cluster #2), Access Control Application on the Reader Node cluster
initiates an API call to Cisco ISE for Role change (Reader -> Author).
2) Cisco ISE upon receiving a role change will request the current Author to release the role of Author. Current Author
(Cluster #1) releases the role of Author (if no sync in progress, else wait until the sync complete) and takes over the role
of Reader Node cluster.
© 2021 Cisco and/or its affiliates. All rights reserved. Page 43 of 51
3) Current Reader (Cluster #2) up for promotion resumes the role of Author Node cluster. Upon the Author and Reader
role change, Cisco ISE updates other Reader Node clusters about the New Author via configuration update. Next, the
new Author Node cluster (Cluster #2) initiates the data migration from Cisco ISE and disables Promote to Author option
in the UI.
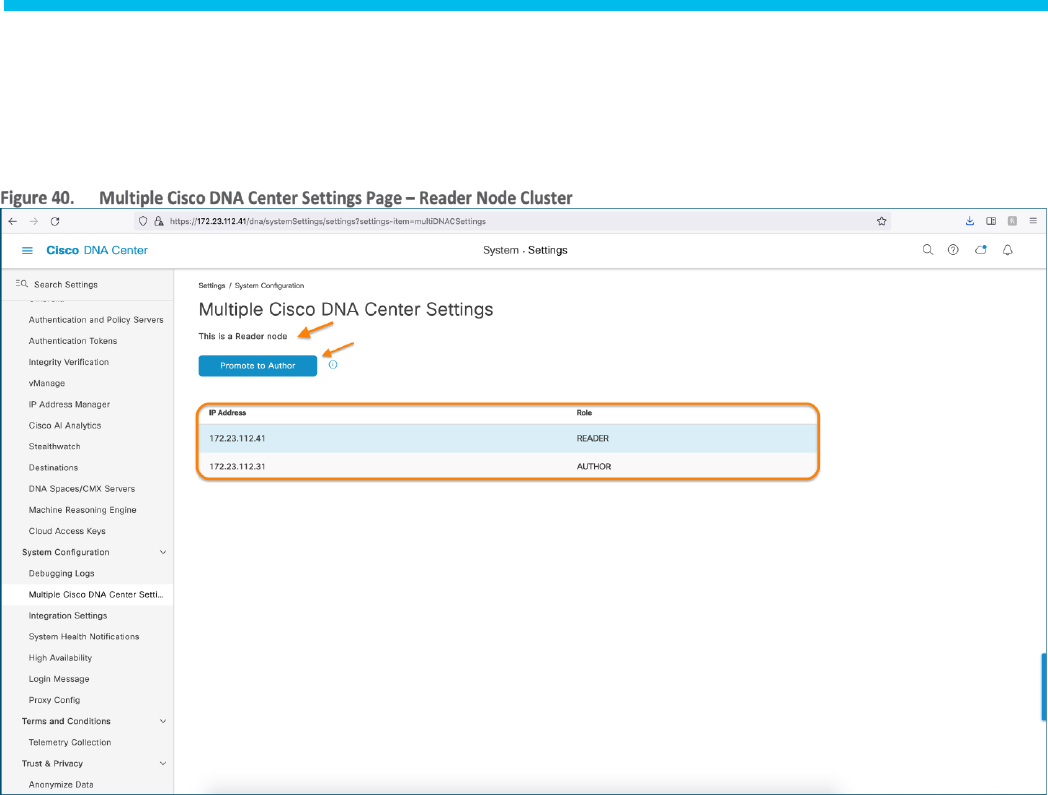
Step 1. On the Reader Node cluster, navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center
Settings and verify the Author and Reader Node roles.
Step 2. Click on Promote to Author button and upon clicking, below warning messages appears.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 44 of 51
Step 3. Click Continue to promote the node to Author role.
The transition process may take several minutes.
Step 4. Verify that the Cluster this was promoted changes to the Author Role as show in Figure 43.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 45 of 51
Step 5. Verify that the previous Author Node cluster is now in the Reader Node role as show in Figure 44.
Step 6. Once the promotion operation in successful, start the migration operation on the Author Node cluster to initiate
policy migration from ISE.
Depending on the amount of Policy data, this process may take up to an hour.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 46 of 51
Force Promotion of Reader Role to Author Role
Force Promotion is a form of manual promotion that is intended to promote the current Reader Node cluster. The Force
Promote option only appears during the Graceful Promotion process. Force Promotion should only be used in the following
situations:
●
The current Author Node cluster is out of service
●
The current Author Node cluster is unresponsive
●
The Reader-Node-to-Author-Node graceful promotion is taking more than five minutes
Do not use the Force Promotion option while the existing Author Node cluster is in service, as this may result in data loss and the
Author Node cluster getting out of sync with ISE. It is strongly recommended that Force Promotion is used only if service must
be restored immediately, and any data loss is acceptable.
After the Forced Promotion operation, the promoted Reader Node cluster becomes the new Author Node cluster for the
deployment. When a former Author Node cluster becomes available, it will transition to the Reader Node role and download the
latest configuration data from ISE.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 47 of 51
Upon initiating the promotion of a Reader Node cluster (Cluster #2), Access Control Application on the Reader Node cluster
initiates an API call to Cisco ISE for Role change (Reader -> Author). Upon receiving a role change, Cisco ISE will request the
current Author to release the role of Author. If the current Author (Cluster #1) is unresponsive and if the administrator selects
Force Promotion, Reader Node cluster ACA package initiates API call with FORCE FLAG and this would change the Reader Node
cluster to Author and Author to Reader role immediately in Cisco ISE. The Configuration update message is sent to all nodes.
Next, the new Author Node cluster (Cluster #2) initiates the data migration from Cisco ISE and disables Promote to Author
Option in the UI.
The steps to Force Promote a Reader Node cluster to Author Node cluster are the same as called out in the Graceful Promotion
section, except an additional step after Step 4 to initiate the Force Promotion. A summary of these steps without screen shots
are below:
Step 1. On the Reader Node cluster, navigate to ☰ > System > Settings > System Configuration > Multiple Cisco DNA Center
Settings and verify the Author and Reader Node roles.
Step 2. Click on Promote to Author button and upon clicking, below warning messages appears.
Step 3. Click Continue to promote the node to Author role.
The transition process may take several minutes.
Step 4. Click the Force Promote button shown in Figure 47.

© 2021 Cisco and/or its affiliates. All rights reserved. Page 48 of 51
Multiple Cisco DNA Center Troubleshooting
Troubleshooting the Multiple Cisco DNA Center to ISE feature can be completed using logs from Cisco DNA Center and ISE.
Compilation, Interpretation, and correlation of these logs should be performed with assistance from the Cisco Technical
Assistance Center (TAC).
Cisco DNA Center Logs
Cisco DNA Center logs are accessed from the appliance (maglev) CLI. These should only be accessed with assistance from the
Cisco TAC.
●
Network-design-service—Events corresponding to Cisco ISE Connectivity
●
Identity-manager-pxGrid-service—pxGrid related subscription, registration, and bulk download
Aca-controller-service—Migration, runtime sync, promotion, registration, and entity specific events such as Scalable
Groups, Access Contracts, Policy, Scalable-Group-to-VN association.
Cisco ISE Logs
Cisco ISE logs are accessed from the ISE GUI. In ISE:
●
Navigate to Operations > Troubleshoot > Download Logs > Select Node > Debug Logs > Ise-psc.log
●
Navigate to Administration > System > Logging > Debug log configuration and set PxGrid, Infrastructure, and ERS logs to
debug.
●
Navigate to Operations > Troubleshoot > Download Logs > Select PxGrid Node > Debug Logs > Pxgird-server.log

© 2021 Cisco and/or its affiliates. All rights reserved. Page 49 of 51
Appendix A: Hardware and Software Versions
The following products and software versions were included as part of validation in this deployment guide, and this validated set
is not inclusive of all possibilities. Additional hardware options are listed in the associated Software-Defined Access Solution
Design Guide, the SD-Access Compatibility Matrix, and the Cisco DNA Center data sheets that may have guidance beyond what
was tested as part of this guide. Updated Cisco DNA Center package files are regularly released and available within the
packages and updated listings.
Table 4. Cisco DNA Center
Product
Part number
Software Version
Cisco DNA Center Appliance
DN2-HW-APL & DN2-HW-APL-L
2.2.2.3
All packages running on the Cisco DNA Center during validation are listed—not all packages are included as part of the testing
for SD-Access validation.
Table 5. Cisco DNA Center Package Versions
Package Name – CLI
Package Name – GUI
Software Version
sd-access
SD Access
2.1.363.60202
access-control-application
Access Control Application
2.1.363.60202
group-based-policy-analytics
Group-Based Policy Analytics
2.2.1.209
multi-dnac-enablement
Multiple Cisco DNA Center
2.1.360.60878
Table 6. Device Platform, Model, and Software Version
Platform
Model (PID)
Software Code Version
Cisco DNA Center
DN2-HW-APL and DN2-HW-APL-L
Cisco DNA Center 2.2.2.3
Identity Services Engine
R-ISE-VMS-K9
ISE 2.6 Patch 7
Catalyst 9000 Series Switches
C9300-48U
17.3.2a

© 2021 Cisco and/or its affiliates. All rights reserved. Page 50 of 51
Appendix B: References Used in this Guide
Cisco DNA Center Second-Generation Appliance Installation Guide, Release 2.2.2:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/2-2-
2/install_guide/2ndgen/b_cisco_dna_center_install_guide_2_2_2_2ndGen.html
Cisco DNA Center Security Best Practices Guide: https://www.cisco.com/c/en/us/td/docs/cloud-systems-
management/network-automation-and-management/dna-center/hardening_guide/b_dnac_security_best_practices_guide.html
Cisco Identity Services Engine Installation Guide, Release 2.6: https://www.cisco.com/c/en/us/td/docs/security/ise/2-
6/install_g;uide/b_ise_InstallationGuide26.html
Cisco DNA Center SD-Access LAN Automation Deployment Guide: https://www.cisco.com/c/en/us/td/docs/cloud-systems-
management/network-automation-and-management/dna-center/tech_notes/b_dnac_sda_lan_aut;omation_deployment.html
Cisco SD-Access Macro-Segmentation Deployment Guide:
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sda-macro-segmentation-deploy-guide.html
Cisco DNA Center Group-Based Policy Deployment Guide: https://community.cisco.com/t5/networking-documents/group-
based-policy-analytics-deployment-guide/ta-p/4096076
Cisco DNA Center & ISE Management Infrastructure Deployment Guide:
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-dnac-ise-deploy-guide.html

