

Francesca Martucci
Technical Solutions Architect, Cybersecurity EMEA
ISE Planning, Staging and
Deployment
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
“A goal
4
BRKSEC-2660
Antoine de Saint-Exupéry
without a plan
is just a wish”

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Deploying any network access
control solution is crucial
but it isn’t easy….
BRKSEC-2660
5

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
What needs to be included in my planning?
6
BRKSEC-2660
Architecture
Use cases
Network Devices
capabilities
Endpoint
discovery
Segmentation
method
802.1x
configuration
Backup plan
Other teams
point of contacts
Management
support
Business
objectives
Password or
Certificates
Supplicant
configuration
Policy sets
AD groups
Growth plan
Posture policies
Custom profiles
NAD OS
upgrade
Test
environment
CMDB
integration
End user
involvement
…
…
…
…

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Deploying any network access
control solution is crucial
but it isn’t easy….
BRKSEC-2660
7
Proper planning is essential
to a successful deployment.

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Who am I?
Technical Solutions Architect
Cyber Security EMEA
In Cisco since 24 years...
... And 3 countries
Main interest on
• Policy and Access
• Segmentation
• Industrial Security
BRKSEC-2660
8

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
9
Cisco ISE High Level Design
BRKSEC-2660
Business Objectives
Environment
(Network Device vendor, supplicants, PKI)
Scenarios & Use Cases
( Posture, BYOD, Device Administration)
Policy Details
( External Identity Sources, what type of posture
what type of BYOD
Operations & Management
Scale & High Availability

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
10
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
What not to expect:
11
• Specific ISE use cases and their implementation
• Detailed configuration guidelines
• Troubleshooting information
• Licensing
BRKSEC-2660

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
12
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
What are your business priorities?
Device Administration
Secure Access
Guest Access
Asset Visibility
Compliance & Posture
Context Exchange
Segmentation
Cisco SDA/DNAC
Threat Containment
BYOD
ISE
Do you need a BYOD policy?
Which use cases could be
considered for the future?
Profiling is critical with today
IoT proliferation
What is the business trying
to accomplish with ISE?
From where do you want to
start?

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Defining your Security Policy
What is an IT security policy?
“It identifies the rules and procedures for all
the individuals accessing and using an
organization’s IT assets and resources.”
BRKSEC-2660
14

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Government
Financials
Healthcare
Retail Education
Transportation
Services Utilities Technology Manufacturing
Everyone Has Different Needs
BRKSEC-2660
15

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Example of your ISE policy planning
Endpoint Type Authentication Identity Store Network Access Enforcement Staging / Provisioning
Corp PC
802.1X – Cert ISE Cert Store Full Access VLAN CORP Physical Staging Port
Guests
WebAuth ISE Guest DB Internet-Only VLAN Guest
Manual Connect
Sponsored account
Access Point
802.1X – User/Pass ISE User DB Trunk Trunk AP Provisioning
AP Provisioning
MAB ISE MAC Whitelist WLC-Only VLAN AP ISE Profiling
Printers
MAB ISE MAC Whitelist Print Servers-Only VLAN Printers ISE Profiling
Network TeamEndpoint Team Security Team
Remember: do not think only at positive outcome.
What if a corporate PC certificate is expired?
BRKSEC-2660
16

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Interoperation with other teams
• Management buy in is critical to have support of your decisions
• Get the right contacts in the other teams ahead of time
• Monitor and update polices with your IT Security Policy
Get
management
support
Write policies
Implement
policies
Monitor
policies
BRKSEC-2660
17
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Understand Your Needs and Use cases
Management & Operations
• Top Down / Bottom Up?
• Org(s) / Regions / Departments
• Collaboration or Siloes
• Scheduling Config Changes
• Tooling & Automation
Scaling
• Concurrent Active Endpoints
• Scale Horizontally
• Scale Vertically
• Geography
Environment
• Wired / Wireless / VPN
• Multi-Vendor
• Hardware & Software
• Network Device Capabilities
Objectives / Risk / Priorities
• Brand Trust
• Customer/Patient Data
• Hospitality: Fast & Easy
• IT/OT Segmentation
• Protect Intellectual Property
BRKSEC-2660
18

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
20
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Monitoring & Troubleshooting Node
(MNT)
• Receives logs from all nodes
• Handles remote logging targets
• Generates summary Dashboard Views
• Performs scheduled reports
• Handles reporting and API queries
Platform Exchange Grid Node (PXG)
• Runs pxGrid controller
• Authorizes pxGrid Pubs/Subs
• Publishes pxGrid topics to subscribers
• Handles ANC/EPS requests
• REST APIs
Policy Service Node (PSN)
• TACACS requests
• RADIUS requests
• Endpoint profiling probes
• Identity store queries
• Hosts Guest/BYOD portals
• MDM/Posture queries
• TC-NAC & SXP services
Policy Administration Node (PAN)
• Administrative GUI
• Policy configuration
• Policy replication
• Centralized Guest database
• Centralized BYOD database
• Configuration REST APIs
21
ISE Personas
BRKSEC-2660
ISE

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Employee VLAN-100
If then
Contractor SGT-20
If then
Things ACL-300
If then
Authorization Policy
Config Sync
RADIUS, TACACS+,
Profiling, etc.,
PSN
ISE Node Personas… Explained
22
BRKSEC-2660
*PSNs can optionally be behind a load-balancer and can be accessed via Load Balancer Virtual IP address (VIPs)
Exchange Topics
TrustSecMetaData
SGT Name: Employee = SGT-10
SGT Name: Contractor = SGT-20
...
SessionDirectory
Bob with Win10 on CorpSSID
Context
Partner Eco System
SIEM, MDM, NBA, IPS, IPAM, etc.
Context (pxGrid)
SIEM
Optional
Context
ISE PSN IP address* =
AAA RADIUS server
Logs
PAN
MNT
Admin
PXG
UI
Configure
ANC = Adaptive Network Control

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Architecture
23
BRKSEC-2660
Distributed ISE
Network
Standalone ISE
pxGrid Controller
• Max 4 in deployment
Policy Administration Node (PAN)
• Max 2 in a deployment
Policy Services Node (PSN)
• Max 50 in a deployment
Monitoring & Troubleshooting Node (MnT)
• Max 2 in a deployment

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Distributed Deployment Scale
24
BRKSEC-2660
3700
3600
Same for physical and virtual deployments
Compatible with load balancers
http://cs.co/ise-scale
100 Endpoints
100 Endpoints
Standalone
(for Lab and
Evaluation)
Up to 50,000 Endpoints
Up to 50,000 Endpoints
Small HA
Deployment
2 x (PAN+MNT+PSN)
Medium Multi-node
Deployment
2 x (PAN+MNT+PXG), <= 6 PSN
Up to 2,000,000 Endpoints
Up to 2,000,000 Endpoints
Large Deployment
2 PAN, 2 MNT, <=50: PSNs
+ <= 4 PXGs
3.0+
<=50: PSNs + <= 4 PXGs
Up to 150,000 Endpoints
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Fully Distributed Architecture
Centralize in DCs…or Distribute PSNs across Geographies
25
BRKSEC-2660
Primary PAN & MNT
DC1
Secondary PAN &
MNT
DC2
• Latency should be 300ms round trip between
PAN and PSN
• Bandwidth most critical between:
• PSNs and Primary PAN (DB Replication)
• PSNs and MnT (Audit Logging)
• Co-locate PSNs with AD

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Maximum Concurrent Active Endpoints
26
BRKSEC-2660
ISE
• One endpoint is a unique MAC address
• ISE Licensing is counted by active endpoint
sessions
• RADIUS Accounting defines session Start &
Stop events
• Sessions Start upon RADIUS Authorization
• Sessions Stop upon :
• Disconnect
• Session Expiration
• Idle Timeout

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Nodes – Mix and Match
27
BRKSEC-2660
Physical Appliances Virtual Machines Cloud Instances
SNS-3715
SNS-3755
SNS-3795
SNS-3615
SNS-3655
SNS-3695

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Reminders
ISE platforms
BRKSEC-2660
SNS 3515
SNS 3595
SNS 3615
SNS 3655
SNS 3695
SNS 3715
SNS 3755
SNS 3795
Traditional VM
AWS
Azure & OCI
3.3
3.2
3.1
3.0
2.7
EOL
EOL
28

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Performance & Scale
• Deployment Architectures: S / M / L
• Maximum Concurrent Active Sessions
• Deployment Scale Limits
• Protocol Performance
• Scenario Performance
• PxGrid and SXP scaling
• Network Device maximum numbers
cs.co/ise-scale
BRKSEC-2660
29
Go to page to check for current numbers
Platform
Concurrent active
endpoints supported
by a dedicated PSN
(
Cisco ISE node has
only PSN persona)
Concurrent active
endpoints supported
by a shared PSN
(Cisco ISE node has
multiple personas)
Extra Small
(VM only)
12.000 unsupported
SNS 3615 25,000 12.500
SNS 3715 50,000 25.000
SNS 3655 50,000 25.000
SNS 3755 100,000 50,000
SNS 3695 100,000 50,000
SNS 3795 100,000 50,000

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
30
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
TACACS+ Deployment Models
Separating RADIUS & TACACS+ ISE Cubes?
32
BRKSEC-2660
There are three different options:
Separate ISE cubes
Mixed ISE cube with
separate PSNs
Mixed ISE cube with
shared PSNs
RADIUS
TACACS+
RADIUS
TACACS+
RADIUS
TACACS+
• Scalability is transactions per second (TPS)
• Authentication or also Commands Authorization?
• Do you use scripts?

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
34
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Certificates
❑ System Certificates
• Identifies a cisco ISE node & services
• Specific to the node
• Can manage all node’s system certs from PPAN
❑ Trusted Certificates
List of CAs
• Trusts for the identities of entities interacting with ISE
• Replicated to all the nodes in deployment
❑ ISE Issued Certificates
• Internal CA service
• Issues and manages certificates for endpoints,
pxGrid and ISE messaging
BRKSEC-2660
35

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Endpoint
(Supplicant/Client)
Network Device
(Authenticator)
AAA Server
(Authentication Server)
Identity and
Security Services
ISE
802.1X
VPN
RADIUS
Different ISE System certificates
EAP Tunnel
✅ EAP Authentication
✅ RADIUS DTLS
TLS Tunnel
✅ ISE Admin (GUI plus Node communication)
HTTPS / TLS
✅ Portals
HTTPS / TLS
✅ SAML
HTTPS / TLS
<SAML>
✅ BYOD
✅ SCEP
HTTPS / TLS
✅ pxGrid
HTTPS / TLS
CA
BRKSEC-2660
36

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Systems and Trusted Certificates
Each ISE node has its
own System Certificate
Store
Which ISE role is using
the certificate
Self signed certificate
BRKSEC-2660
37

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Systems and Trusted Certificates
Each ISE node has its
own System Certificate
Store
Which ISE role is using
the certificate
To install certificate
Self signed certificate
BRKSEC-2660
38

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-2660
39

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Controlled Application Restart
From ISE 3.3, the reboot can be scheduled
for each node.
Up to ISE 3.2 a new ISE admin certificate requires
reboot of all the nodes without any control.
Reboot must take place
within 15 days
ISE 3.3.0
BRKSEC-2660
40
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
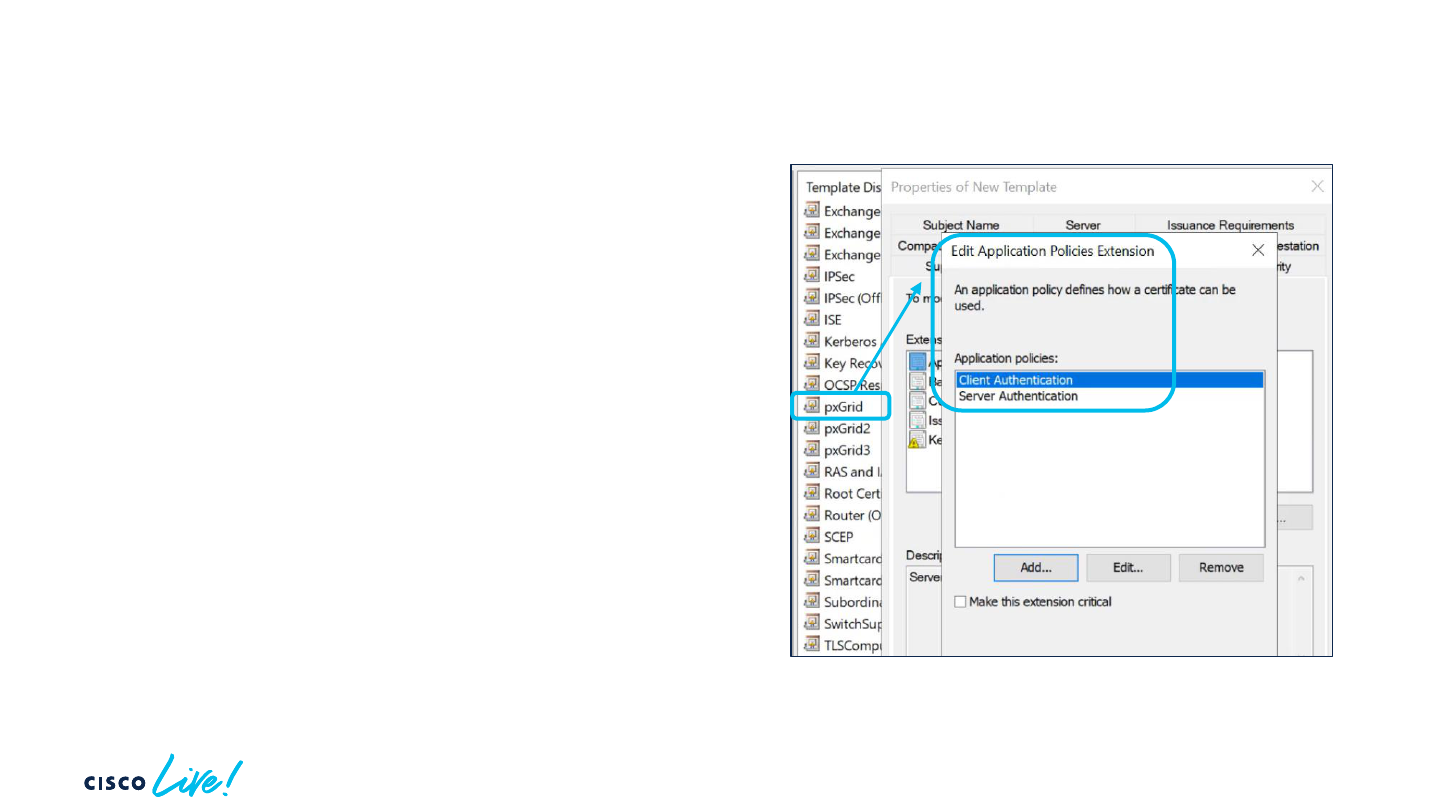
PxGrid Certificate
PxGrid certificate is built with both
Client Authentication and Server
Authentication extension
41
BRKSEC-2660
Need to create your template and
use it for the Signing Request

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
42
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Network Device discovery/capabilities
• Hardware model
• IOS version
• Count
• OS Version and capabilities
• Hardware limitations
√ : Fully supported
X : Not supported
! : Limited support, some
functionalities are not
supported
cs.co/nad-capabilities
BRKSEC-2660
43
Refer to Cisco Compatibility Matrix
2

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Does ISE Support my third-party Network device?
Does my third-party Network Device Supports ISE?
45
BRKSEC-2660
Check for Advanced capabilities support:
• CoA (RADIUS or SNMP)
• URL Redirection
From the Network Component Compatibility, Release 3.3
https://www.cisco.com/c/en/us/td/docs/security/ise/3-3/compatibility_doc/b_ise_sdt_33.html
Might need to:
• Import a Vendor Specific Dictionary
• Create Network Device Profile

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Third party Device support
BRKSEC-2660
46

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Default Network Device Groups (NDGs)
Default NDGs
Maximum 6 Levels
Create Your Own Root NDGs
BRKSEC-2660
47
Location
Organi
zation
Vendor
Use
Case
Type of
access

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Additional Tips
• Always Test before implementing!
• Standardize! Standardize! Standardize!
▪ IOS versions
▪ AAA configuration
▪ Wireless configuration
▪ Profiling configuration
• 3rd party device documentation
BRKSEC-2660
48

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
50
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Endpoints: Native 802.1X Supplicants
wpa_supplicant
NAME
wpa_supplicant - Wi-Fi Protected Access client and IEEE
802.1X supplicant
SYNOPSIS
wpa_supplicant [ -BddfhKLqqsTtuvW ] [ -iifname ] [ -cconfig
file ] [ -Ddriver ] [ -PPID_file ] [ -foutput file ]
OVERVIEW
Wireless networks do not require physical access to the
network equipment in the same way as wired networks.
This makes it easier for unauthorized users to passively
monitor a network and capture all transmitted frames.
In addition, unauthorized use of the network is much
BRKSEC-2660
51

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Windows 7, 8/8.1, and 10 – Native Supplicant
• Now you can do TEAP directly in Windows for Chaining
(Windows 10 build 2004 and ISE 2.7 Patch 2)
• Involve the Active Directory Team
• Group Policy for:
o Supplicant configuration
o Pushing certificates
o Pre-configure SSIDs – better user experience
BRKSEC-2660
52

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
53
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Endpoints: Everything Else
BRKSEC-2660
54

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Endpoint Profiling
Identifies dynamically the devices that connect to your network
ISE Data Collection Methods for Device Profiling
Active Probes: Netflow | DHCP | DNS | HTTP | RADIUS | NMAP | SNMP | AD
Device Sensor: CDP| LLDP | DHCP | HTTP | H323 | SIP | MDNS
Cisco Secure Client (formerly AnyConnect): ACIDex
Feed Service
(Online/Offline)
Endpoints send
interesting data,
that reveal their
device type
ACIDex
ISE
DS
DS
BRKSEC-2660
55

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of RADIUS Probe
OUI = Vendor ID, IP = xx.xx.xx.xx
OUI = Cisco, IP = xx.xx.xx.xx
Cisco Device
HP Device
Apple Device
OUI = HP, IP = xx.xx.xx.xx
OUI = Apple, IP = xx.xx.xx.xx
vendor
BRKSEC-2660
56

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of SNMP Probe
OUI = Random, IP = xx.xx.xx.xx
OUI = Cisco, IP = xx.xx.xx.xx,
Cisco IP Phone 9971
HP Device
Apple Device
OUI = HP, IP = xx.xx.xx.xx
OUI = Apple, IP = xx.xx.xx.xx
Unknown
CDP:cdpCachePlatform = Cisco IP Phone 9971
Cisco Device
BRKSEC-2660
57

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of DHCP Probe
OUI = Random, IP = xx.xx.xx.xx,
OUI = Cisco, IP = xx.xx.xx.xx, CDP:cdpCachePlatform = Cisco IP Phone 9971,
Cisco IP Phone 9971
HP Printer
Apple Device
OUI = HP, IP = xx.xx.xx.xx,
OUI = Apple, IP = xx.xx.xx.xx,
Microsoft Workstation
dhcp-class-identifier CONTAINS MSFT
DHCP:dhcp-class-identifier CONTAINS CP-9971
DHCP:dhcp-class-identifier CONTAINS LaserJet
Unknown
Unknown
DHCP:dhcp-DHCP:dhcp-parameter-request-list EQUALS 1, 3, 6, 15, 119, 252
Apple iDevice
BRKSEC-2660
58

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of DHCP Probe
OUI = Random, IP = xx.xx.xx.xx,
OUI = Cisco, IP = xx.xx.xx.xx, CDP:cdpCachePlatform = Cisco IP Phone 9971,
Cisco IP Phone 9971
HP Printer
Apple Device
OUI = HP, IP = xx.xx.xx.xx,
OUI = Apple, IP = xx.xx.xx.xx,
Microsoft Workstation
dhcp-class-identifier CONTAINS MSFT
DHCP:dhcp-class-identifier CONTAINS CP-9971
DHCP:dhcp-class-identifier CONTAINS LaserJet
DHCP:dhcp-DHCP:dhcp-parameter-request-list EQUALS 1, 3, 6, 15, 119, 252
BRKSEC-2660
59

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of HTTP Probe
OUI = Random, IP = xx.xx.xx.xx, dhcp-class-identifier CONTAINS MSFT,
OUI = Cisco, IP = xx.xx.xx.xx, CDP:cdpCachePlatform = Cisco IP Phone 9971,
DHCP:dhcp-class-identifier CONTAINS CP-9971
Cisco IP Phone 9971
HP Printer
OUI = HP, IP = xx.xx.xx.xx, DHCP:dhcp-class-identifier CONTAINS LaserJet
OUI = Apple, IP = xx.xx.xx.xx,
Windows10-Workstation
IP:User-Agent CONTAINS Windows NT 10.0
IP:User-Agent contains iPad
Microsoft Workstation
Apple iDevice
DHCP:dhcp-DHCP:dhcp-parameter-request-list EQUALS 1, 3, 6, 15, 119, 252
BRKSEC-2660
60

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of NMAP Probe
OUI = Random, IP = xx.xx.xx.xx, dhcp-class-identifier CONTAINS MSFT, IP:User-
Agent CONTAINS Windows NT 10.0, FQDN=test-laptop1.zero0k.org,
OUI = Cisco, IP = xx.xx.xx.xx, CDP:cdpCachePlatform = Cisco IP Phone 9971,
DHCP:dhcp-class-identifier CONTAINS CP-9971, FQDN=test-
phone1.zero0k.org
Cisco IP Phone 9971
Apple IPad
OUI = HP, IP = xx.xx.xx.xx, DHCP:dhcp-class-identifier CONTAINS LaserJet,
FQDN=test-printer1.zero0k.org,
OUI = Apple, IP = xx.xx.xx.xx, IP:User-Agent contains iPad, FQDN=test-i-
pad1.zero0k.org
Windows10-Workstation
NMAP:SMB.operating-system CONTAINS Windows 10
NMAP:hrDeviceDescr CONTAINS HP LaserJet P4015
HP Printer
BRKSEC-2660
61

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Effect of AD Probe
OUI = Random, IP = xx.xx.xx.xx, dhcp-class-identifier CONTAINS MSFT, IP:User-
Agent CONTAINS Windows NT 10.0, FQDN=test-laptop1.zero0k.org,
NMAP:SMB.operating-system CONTAINS Windows 10,
OUI = Cisco, IP = xx.xx.xx.xx, CDP:cdpCachePlatform = Cisco IP Phone 9971,
DHCP:dhcp-class-identifier CONTAINS CP-9971, FQDN=test-
phone1.zero0k.org
Cisco IP Phone 9971
HP LaserJet P4015
Apple IPad
OUI = HP, IP = xx.xx.xx.xx, DHCP:dhcp-class-identifier CONTAINS LaserJet,
FQDN=test-printer1.zero0k.org, SNMP:hrDeviceDescr CONTAINS HP LaserJet
P4015
OUI = Apple, IP = xx.xx.xx.xx, IP:User-Agent contains iPad, FQDN=test-i-
pad1.zero0k.org
Windows10-Workstation
AD-OS = Windows 10
BRKSEC-2660
62

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PxGrid Probe Context-in
63
BRKSEC-2660
1. Profiling tool classifies the devices.
2. The attributes are then sent to ISE via pxGrid
3. ISE populates the custom attributes with the ones received
via profiling pxGrid probe
PxGrid
PLC IO DRIVE CONTROLL
ER
Modbus
CIP
PROFINET
…..
CyberVision
Cisco
EA
CyberVision

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Device Sensor to scale attribute collection
ISE
CDP
LLDP
DHCP
MAC
CDP
LLDP
DHCP
MAC
HTTP
DHCP
MAC
RADIUS
accounting
Meraki MS390
MS Switches only
CDP+LLDP
From
AirOS 7.2
Network devices send attributes via
RADIUS to ISE to optimize collection:
Attributes used:
• MAC OUI
• CDP/LLDP
• DHCP
• HTTP (WLC only)
• mDNS,
• H323,
• MSI-Proxy (4k only)
BRKSEC-2660
64
From IOS
15.0(2)SE
ISE

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Wi-Fi Edge Analytics
Disable the ISE Profiling Endpoint Attribute Filter to use
WiFi Device Analytics attributes in policies
ISE 3.3
Apple, Samsung, and Intel
devices are sharing rich
data with the WLCs.
With Catalyst 9800 WLCs
(IOS-XE 17.10) you can
now pass those attributes to
ISE within RADIUS
accounting.
ISE
RADIUS Acct
Model = MacBook
OUI = Apple
= Apple MacBook
Model = iPad
OUI = Apple
= Apple iPad
Model = Galaxy S1
OUI = Samsung
= Samsung
Galaxy S1
BRKSEC-2660
65

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
68
ISE profiles definition
BRKSEC-2660
DHCP:dhcp-class-identifier CONTAINS MSFT
DHCP:dhcp-class-identifier CONTAINS MS-UC-Client
IP:User-Agent CONTAINS Windows
NMAP:operating-system CONTAINS Microsoft Windows
ISE
Endpoint
DHCP
Class-ID: MSFT
HTTP
User Agent: Windows
NMAP
OS: Microsoft Windows
Certainty
Factor
+10
+10
+10

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Multi-Factor Classification on ISE
Feed Service
(Online/Offline)
ISE
MFC-Manufacturer
Cisco Arlo
Apple
Lenovo
IP-Phone
Camera
Laptop
Laptop
MFC-EndpointType
IP Phone 7980
Pro Wireless Cam
MacBook
Pro
Thinkpad 540
MFC-Model
IOS Linux
macOS
12.0.1
Windows
Enterprise
MFC-OS
Profiles are now made up of four factors:
• MFC-Manufacturer
• MFC-Endpoint Type
• MFC-Model
• MFC-OS
ISE 3.3
BRKSEC-2660
69

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
AI Proposed Profiling Policies
ML Groups Endpoints
ML groups endpoints into
clusters of identical of
based on attribute data
Data Forwarded to Cloud
All data on endpoints
(profiled & unknown)
forwarded to ML engine
ML Cloud
Labels Assigned
Users assign labels to
unknown clusters or
accept recommendations
Bosch Coffee
Machine ?
These are Meraki
cameras
ML Cloud
ISE 3.3
•Must forward endpoint attributes to ML
cloud (available 3.2p1)
•Air gapped environments not supported
BRKSEC-2660
70

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
71
BRKSEC-2660
Multi-Factor Classification (MFC)

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Feed service Updates
• Feed service updates MAC OUIs
• Feed service provides new and updated profiles
• Be careful when applying profile updates, check they do not interfere with
the profiles you have been using and your policies
• You will still have unknowns For everything else: custom profiles
BRKSEC-2660
73

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Create custom profiles
• Gather more information
▪ Create more traffic from the device
▪ Run an NMAP scan
▪ Enable more probes
• Find attributes or combinations of
attributes unique to device type
• Focus on:
▪ Attributes found every time the endpoint
connects
▪ Attributes found very early after the
endpoint connects
BRKSEC-2660
74

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Profiles Precedence
75
BRKSEC-2660
Cisco Provided
Profile
Custom
Profile
Existing Cisco Profile
New Customer Profile
CF = 30 CF =?
Custom profiles CF should
be higher than the ones
provided by Cisco. (in
general low number).
Try put custom profiles
above 100
CF >= 30

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Using device profiles and logical profiles in ISE
BRKSEC-2660
78

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Turning Probes Into Profiles, Profiles Into Protection
ISE Authorization Policies
AuthZ
Segmentation
Examples: DHCP-Class-Identifier | MAC OUI | ACIDEX Device
Platform | User Agent
Attributes
AI Proposed
ISE
Cisco provided
Integrations
Admin
created
Wifi edge analytics
Profiles
BRKSEC-2660
79

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Behavioral vs Organizational Endpoint Information
Behavioral
• Probes and profiling
• Device Sensor
• pxGrid Context-In
Organizational
• Endpoint Custom Attributes
• Context Visibility Input (GUI/CSV)
• Custom Attributes and endpoint
REST API (JSON)
• External Databases (CMDBs)
• Active Directory / LDAP
• pxGrid Direct (ServiceNow, etc.)
Attribute Name
Type
Created
Date
Expires
Date
Owner
String
Department
String
iPSK
String
Common Uses
BRKSEC-2660
82

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco ISE pxGrid Direct for CMDBs
ISE 3.2
Cisco ISE
External Database
(E.g., ServiceNow CMDB)
{
}
Server Response (JSON)
ISE Endpoint DB ISE Auth Policy
If
Then,
VLAN:
GET
REST API Request
(Admin can specify APIs to
any REST compatible
server)
3.2
{
"result": [
{
"sys_import_state_comment": "",
"template_import_log": "",
"sys_updated_on": "2022-05-17 10:53:53",
"sys_class_name": "EDDA_Demo",
"sys_target_sys_id": "",
"sys_id": "00021059db6b01101f0f174b13961900",
"sys_updated_by": "aacook",
"sys_created_on": "2022-05-17 10:53:53",
"sys_import_set": "ISET0011307",
"sys_transform_map": "",
"sys_created_by": "aacook",
"sys_import_row": "34,285",
"u_account_name": "Holly.Allen@example.org",
"u_macaddress": "05:0e:33:f3:2b:03",
"sys_row_error": "",
"group_tag": "cts:security-group-tag=2774-000",
"sys_target_table": "",
"sys_mod_count": "0",
"u_hostname": "black.williams.com",
"import_set_run": "",
"sys_tags": "",
"u_community_group": "Administration",
"sys_import_state": "Pending",
"u_config_item": "SNtoDataMartHolly.Allen",
"u_sync": "",
"u_ci_status": "Operational",
"u_host_name": "black.williams.com"
},{ ⋯ }
]
}
BRKSEC-2660
83

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
84
BRKSEC-2660

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
85
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
86
Make use of Policy Sets
BRKSEC-2660
Organizations
Type
Medium
Location
Wireless
RADIUS
Vendor/Model

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Conditions simplification
87
BRKSEC-2660
Use Compound
Conditions and
for custom ones
Pre-sets Dictionary
Condition are easy to
read and intuitive
Custom created
Conditions often are
not as intuitive

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Dynamic Variable Substitution
ID Store
Attribute
• Match conditions to unique values stored per- User/Endpoint in
internal or external ID stores (AD, LDAP, SQL, etc.)
• ISE supports custom User and Endpoint attributes
BRKSEC-2660
88

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Speed Test
Is the image matching the condition set?
• Total stars = 10
• Total Green stars = 4
• Total red stars = 2
• Outer shape = Red triangle
BRKSEC-2660
90

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Auth Policy Optimization
1. AD Groups
2. AD Attributes
3. MDM
4. Certificate
5. ID Group
6. SQL Attributes
7. Auth Method
8. Endpoint Profile
9. Location
Policy Logic:
o First Match, Top Down
o Skip Rule on first negative
condition match
BRKSEC-2660
91
😩

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Auth Policy Optimization
Block 1
Block 2
Block 3
Block 4
4. AD Groups
5. AD Attributes
9. MDM
7. Certificate
6. ID Group
8. SQL Attributes
2. Auth Method
3. Endpoint Profile
1. Location
• Local conditions
should be put
before external
• External lookup
should go at the
end as take more
time
BRKSEC-2660
92
😁

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
CxO
IT Staff
Human
Resources
Everyone Else
Most Specific
Least Specific
AD1·ExternalGroups EQUALS
domain.com/users/HR
AD1·ExternalGroups EQUALS
domain.com/users/Domain Users
AD1·ExternalGroups EQUALS
domain.com/users/IT AND
AD1·ExternalGroups EQUALS
domain.com/users/Domain Power Users
AD1·ExternalGroups EQUALS
domain.com/users/IT AND
AD1·ExternalGroups EQUALS
domain.com/users/Domain Power Users AND
AD1·ExternalGroups EQUALS
domain.com/users/Leadership AND
AD1·ExternalGroups EQUALS
domain.com/users/ELT
93
AD Policy rule optimization example
BRKSEC-2660
• Granular policies (most
restrictive and with higher level
of access) should go first.
• Default/high-level policies go
bottom.

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
94
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Who Needs an ISE Lab? You do!
Customers
Partners
With every Standalone installation :
• 90-day Evaluation license
• For 100 endpoints
• All Cisco ISE features
• 1 TACACS+ license
You can set up a limited deployment and test
all the required features in your environment
BRKSEC-2660
95
Standalone

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Lifecycle Orchestration & Policy Management
Zero Touch
Deployment
Patch
Installation
License
Management
Certificate
Management
Configuration
Management
Policy
Management
Operations
Automation
ISE 3.1
Patch 1 or later
Python Ansible VSCode
network_device:
- name: lab-mr46-1
description: ’’
profileName: Cisco
authenticationSettings:
dtlsRequired: false
enableKeyWrap: false
enableMultiSecret: 'false'
keyEncryptionKey: ''
keyInputFormat: ASCII
#YAML
github.com/CiscoISE
BRKSEC-2660
96

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Deployment and Operational Lifecycle
Configure
Identity Stores
Network Devices
Policy Sets
Endpoints
Portals
…
Destroy
Terminate
…
Provision
VPC
DNS
VPC(s)
Networks
VPNs
ISE Nodes
Patch + Hotpatches
Load Balancers
…
Operate
{⋯}
Manage Endpoints
Reporting
Performance
pxGrid / Events
Backup/Restore
Patch
…
G U E S T
Deploy
Enable APIs
Repositories
Roles
Services
Certificates
Licensing 😁
…
ISE
ISE
ISE
ISE
Extend
BRKSEC-2660
97

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Eternal Evaluation
Cisco ISE playbooks and roles for ISE automated deployment and configuration in labs and
demos, beginning with the ISE Eternal Evaluation (ISEEE)
https://github.com/1homas/ISE_Ansible_Sandbox
• iseee.ssh.yaml
• iseee.provision.yaml
• iseee.facts.yaml
• iseee.patch.yaml
• iseee.deploy.yaml
• iseee.certificates.yaml
• iseee.licensing.yaml
• iseee.configure.yaml
• iseee.backup.yaml
• iseee.restore.yaml
• iseee.extend.yaml
• iseee.password_reset.yaml
• iseee.destroy.yaml
iseee.yaml
BRKSEC-2660
98

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
99
How to test your lab?
BRKSEC-2660
Using real devices (the one you will use in
production) is always best (expecially if
you test use cases like posture/profiling)
BUT…
Sometimes simulation tools are useful
(policy match or simulating large number
of devices).
Try the Session Trace Test tool in ISE

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Where To Start: planning
• ISE Deployment Options
• Certificates
• Network Devices
• Supplicants
• Profiling
• Policies optimization
• Create your own lab
• 802.1x Deployment Modes
103
BRKSEC-2660

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
104
Deployment Modes
BRKSEC-2660
Monitor Mode ( Visibility)
File
Servers
ISE
Campus Network
Port Open
Unconditionally
Pass / Failed
Authentication
No impact to existing network
Low-Impact Mode
(Visibility and Control)
ISE
Campus Network
DHCP DNS
Servers
File
Servers
Before
Authentication
After
Authentication
PREAUTH ACL PERMIT ACL
permit eap dhcp dns
deny any
permit ip any any
Begin to control and
differentiate access
Closed Mode
(Visibility and Control)
ISE
File
Servers
Only EAP
Allowed
Before
Authentication
After
Authentication
Campus Network
• Not everyone needs Closed Mode
• No access at all before
authentication
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
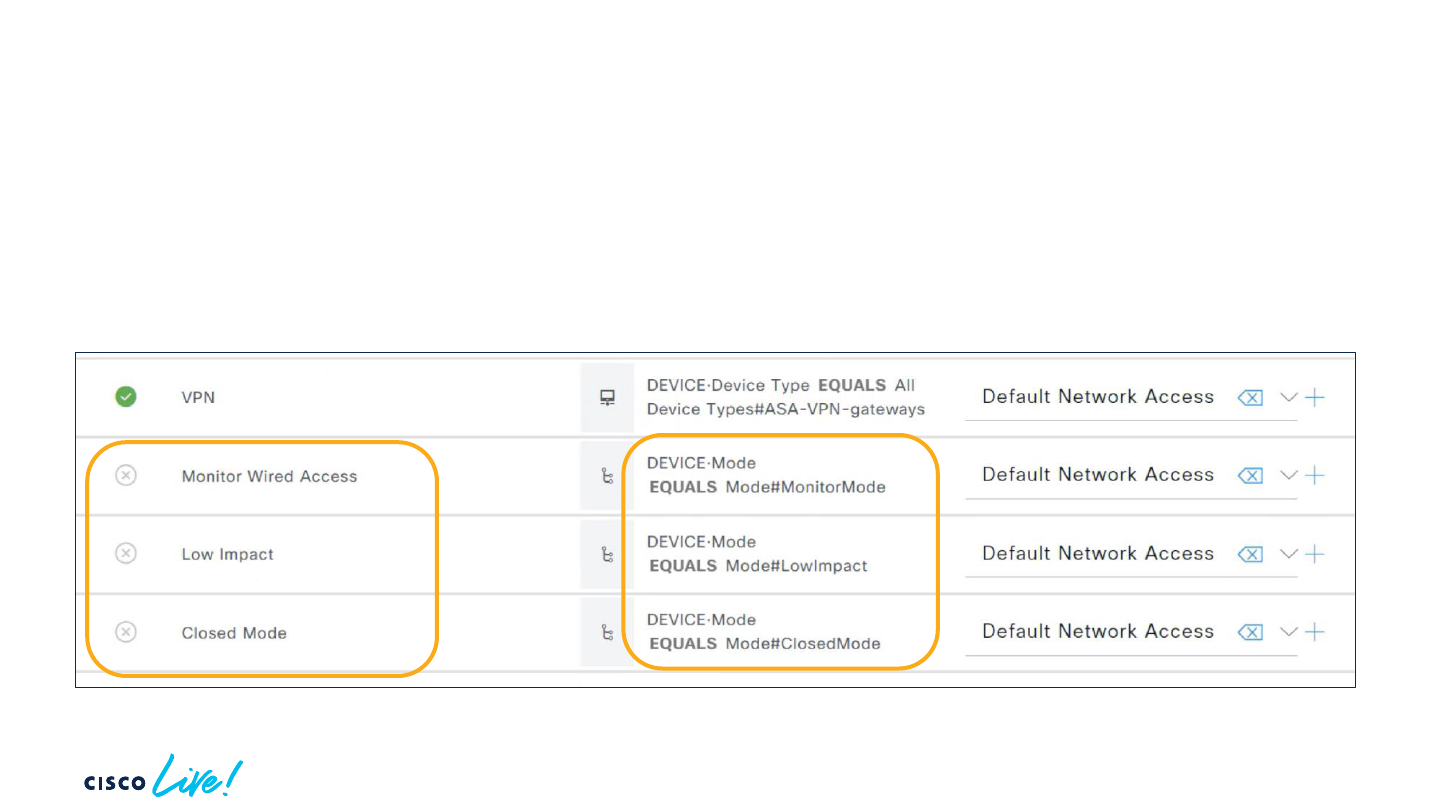
Utilizing Policy Sets with Modes
105
BRKSEC-2660
• When deploying leverage Network Device Groups
• Move devices in and out while the deployment progresses

Day 2
Operations

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
User involvement
User Communication before
and after ISE rollout
BRKSEC-2660
107

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Supporting ISE After Deployment
• Train Your Support with A Playbook for
common issues
• Document as much as possible!
✓ Policy Configuration
✓ Supplicant Configuration
✓ Network Access Devices
BRKSEC-2660
108
• Many document templates available on ISE Communities

Wrap up

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Deploying any network access
control solution is crucial
but it isn’t easy….
Proper planning is essential to
any successful development.
BRKSEC-2660
110

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE learning map
112
BRKSEC-2660
Learn how Cisco ISE will
help you implement
Network access Control in
your campus.
Sessions will cover how to
plan and deploy, how to
leverage the new cloud
capabilities, best practices
and other topics

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco ISE Resources
• Consolidated list of resources
cs.co/ise-resources
• Community Q&A
cs.co/ise-community
• Recorded webinars and other
videos
cs.co/ise-videos
• Integration Guides
cs.co/ise-guides
• Licensing Guide
cs.co/ise-licensing
BRKSEC-2660
113
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Ask The Community
cs.co/ise-community
How to Ask the Community for Help
• The Community is Not TAC
• No Comment on Roadmaps or Fixes
• New Features and Feedback
• Provide Details
• Goal/Scenario?
• NAD Hardware & Software?
• Endpoint OS(es)?
• Browser(s)?
• Reproducibility (expected vs actual)
• Pictures and Video!
BRKSEC-2660
114

Thank youThank you

